Azure OAuth App and SharePoint
Azure ACS (Access Control Service) authentication is deprecated and will stop working on April 2, 2026. Please use Certificate-based authentication for all new integrations. Existing Client Secret integrations should be migrated as soon as possible.
Setting up an Azure OAuth App requires the following:
- Creating the OAuth App
- Optionally restricting the OAuth App to only be able to access specific SharePoint sites
- Granting permission for the OAuth App to use the SharePoint Rest API
Each of these steps is covered in detail below.
Creating an Azure OAuth App
Before you can configure the connector, you must create an OAuth App in the SharePoint Online platform.
The native connector will authenticate to SharePoint as the registered OAuth application/client.
You’ll need to provide values for
- Client ID
- Tenant ID
- Client secret Id
- Client secret value
- Tenant name
- Authentication method: Client Secret (deprecated) or Certificate
- If Client Secret:
- Client secret id
- Client secret value
- If Certificate:
- Certificate file upload
- Certificate password
- If Client Secret:
To get started, first log in to SharePoint Online and access your administrative dashboard ensuring that you are logged in as at least an Azure Portal service account.
Follow these steps:
- Sign in to https://portal.azure.com/ and click on Azure Active Directory.
- Select App Registrations and click New Registration.
- Give the app a name. E.g. "Interact Workplace Search".
- Register the application.
- Make a note of the
Application (client) IDandDirectory (tenant) ID.
Certificate-based authentication
To use certificate-based authentication, you must provide:
- A public certificate to upload to the Azure App Registration
- A private certificate with password to supply when configuring the connector
You may use a certificate issued by your organisation’s certificate authority or a trusted provider. The example below shows how to generate a self-signed certificate using PowerShell.
# Generate a self-signed certificate for SharePoint Online connector authentication
$certName = "SharePointConnector"
$certPassword = Read-Host -AsSecureString -Prompt "Enter a password for the certificate"
# Create certificate
$cert = New-SelfSignedCertificate `
-Subject "CN=$certName" `
-CertStoreLocation "Cert:\CurrentUser\My" `
-KeyExportPolicy Exportable `
-KeySpec Signature `
-KeyLength 2048 `
-KeyAlgorithm RSA `
-HashAlgorithm SHA256 `
-NotAfter (Get-Date).AddYears(2)
# Export certificate with private key (.pfx)
$pfxPath = "$PWD\SharePointConnector.pfx"
Export-PfxCertificate -Cert $cert -FilePath $pfxPath -Password $certPassword
# Export certificate without private key (.cer) for Azure AD
$cerPath = "$PWD\SharePointConnector.cer"
Export-Certificate -Cert $cert -FilePath $cerPath
Write-Host "Certificate created successfully!"
Write-Host "PFX file (private key, upload to Interact): $pfxPath"
Write-Host "CER file (public key, upload to Azure AD): $cerPath"After generating the certificate:
- Navigate to Certificates & Secrets.
- Go to Certificates and Upload certificate (public key file).
- Keep the private key and password securely, you will need to provide it when configuring the SharePoint Online Workplace Search connector
Ensure the certificate remains valid and is rotated before expiry. The example script above generates a certificate with a two-year validity period.
Configuring the Workplace Search Connector
You can then enter the credentials into the SharePoint Online Connector
The TenantName for the SharePoint Online Connector should be the name of the tenant.
For example, if your tenant is contoso.onmicrosoft.com, then you would enter contoso. So, it should look like:
{
"AuthenticationType": "Certificate",
"ApplicationClientId": "[Your ApplicationClientId]",
"DirectoryTenantId": "[Your DirectoryTenantId]",
"TenantName": "contoso",
"CertificatePassword": "[Your CertificatePassword]"
}You will also need to upload the private key certificate on the Workplace Search Connector configuration page.
Configuring Permissions
Next, you will have to set up the permissions for the OAuth App.
- Navigate to API Permissions and click Add Permission.
- Add the following application permissions:
- Graph API
Sites.Read.All- Is used to fetch the sites and their metadata
- (See "Restricting OAuth App API Permissions to Specific Sites" for more detail)
Files.Read.All- Is used to fetch the sites and their metadata
Group.Read.All- Is used to fetch groups for document-level permissions
User.Read.All- Is used to fetch user information for document-level permissions
- SharePoint
Sites.FullControl.All- (See "Restricting OAuth App API Permissions to Specific Sites" for more detail)
- Graph API
Sites.FullControl.All permission is required for SharePoint in order to read existing site permission assignments via the SharePoint REST API. The permission is needed solely because SharePoint restricts access to permission metadata unless Full Control is granted.
The connector performs read-only operations and does not add, remove or alter users, groups or roles on the site.
Depending on how you want to use the native connector, its possible to synchronise Team Sites (Group Sites) without any additional OAuth App permissions by listing them individually within the config, as explicit sites that you want to synchronise.
But, if you want to configure the connector to automatically discover all team sites and synchronise them all (apart from an optional set of disallowed team sites), then you will also need to add the following permissions to the OAuth App:
- Graph API
Team.ReadBasic.AllTeamSettings.Read.AllTeamSettings.ReadWrite.All
You will need to get someone with admin permissions to grant admin consent, using the Grant Admin Consent link from the permissions screen.
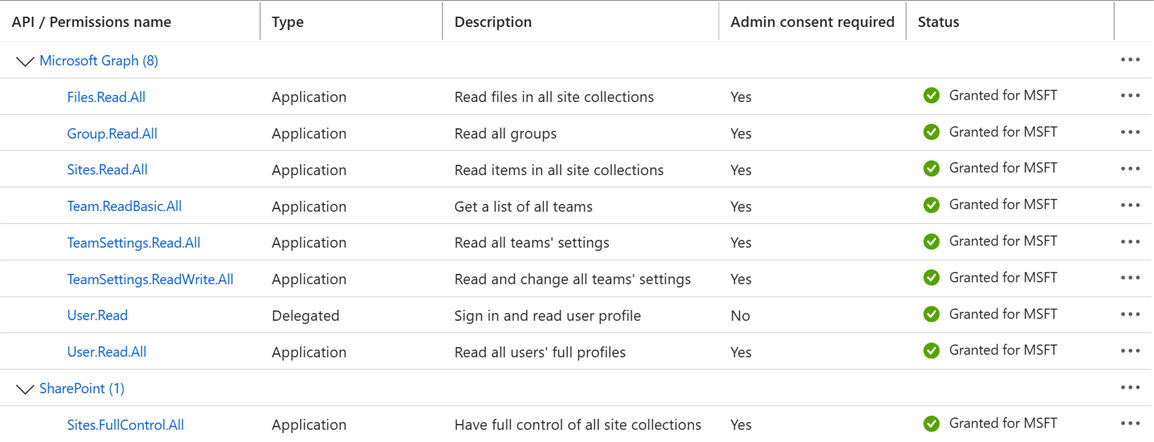
Save the tenant name (or Domain name) displayed from within Azure.
Restricting OAuth App API Permissions to Specific Sites
The Sites.Read.All permission scopes, which are set within the Microsoft Graph and the SharePoint APIs, will allow the app registration to access all sites within your tenant. However, it can be preferable to only allow the app to access specific sites.
Beyond the initial "Creating an Azure OAuth App" process, the following steps can be taken so that the OAuth App only has access to specific sites.
- Modify the Azure OAuth API Permission Scopes to include
Sites.Selectedinstead ofSites.Read.All - Grant access for the Azure OAuth App to be able to access the sites that you want to synchronise
- Update the SharePoint Online Native Connector to no longer perform automatic site collection discovery (which it performs by default) and instead only connect to a specified site collection.
Modifying the API Permission Scopes
This can be achieved by using the Sites.Selected scope instead of the Sites.Read.All scope for the Microsoft Graph API and the Sites.FullControl.All scope for the SharePoint API.
If modifying an existing app registration to only access selected sites, then be sure to fully remove theSites.Read.Allscopes from both the Microsoft Graph and SharePoint APIs and also ensure you subsequently remove any corresponding admin consent for those permissions. Failing to do this will result in the app registration still being able to access all sites.
Once the permissions have been set they should look like:
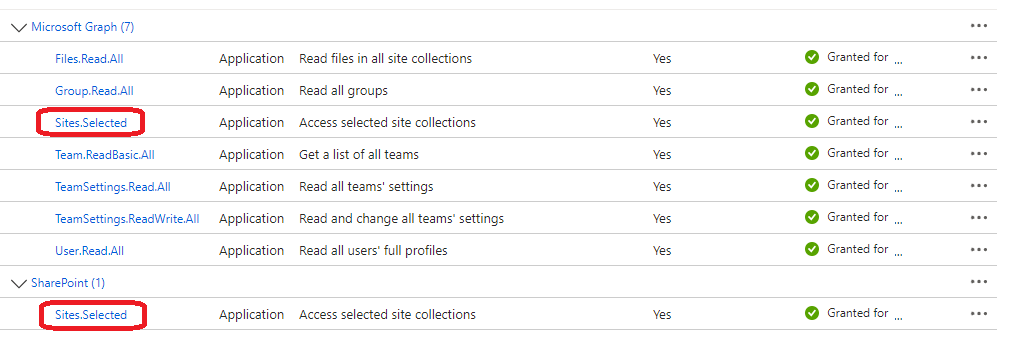
As a result of making these changes, the connector will no longer be able to discover site collections or sites. Additional steps must be taken before the connector is able to access the sites for synchronisation.
Granting OAuth App Permissions to Specific Sites
The following links by Microsoft describe in detail how to granting permission for an OAuth App to access a specific Site Collection using either the Graph API (Explorer) or PowerShell:
- Understanding Resource Specific Consent for Microsoft Graph and SharePoint Online | Microsoft Learn
- Controlling app access on a specific SharePoint site collections is now available in Microsoft Graph - Microsoft 365 Developer Blog
For the purposes of the guides above, here's how you can find the id of your site:
-
Navigate to your Site and append
/_api/site/idto the URL. You should end up with this URL:https://<your_tenant_name>.sharepoint.com/sites/<your_site_name>/_api/site/id -
Grab Edm.Guid from the response.
-
Navigate to
https://<your_tenant_name>.sharepoint.com/_api/v2.1/sites/<edm_guid> -
JSON response will contain the ID property. That's the full ID of your site.
Note: When granting site permissions, make sure to assign the
FullControlrole to the target sites. It is the minimum permission level that allows an application to enumerate permission metadata using supported APIs.
Configuring the Connector to No Longer Perform Automatic Site Collection Discovery
The SharePoint Online Native Connector by default performs a Graph API request to fetch a list of site collections as part of its synchronisation process. This call is no longer allowed (Access Denied) if the Sites.Read.All permission scope has been removed and replaced with the Sites.Selected.All permission score.
Therefore, it is neccesary to update the connector config JSON to to change the site collection discovery mode to be Specific rather than AutomaticDiscovery (which is the default value).
This will be achieved by adding the following json into the root of the configuration JSON.
"SiteCollectionOptions" : {
"Mode" : "Specific"
"WebUrl" : "[The url of the site collection]"
}Using the Specific mode will mean that the connector will no longer perform the automatic site collection discovery, and instead will only connect to the site collection specified by the WebUrl parameter.
The WebUrl should be set to your SharePoint Site Collection URL. For example: https://contoso.sharepoint.com
Security considerations when using Sites.Selected with Files.Read.All
Sites.Selected with Files.Read.AllWhen using Sites.Selected, the only Files permission that allows access to files is the Files.Read.All permission. Other options such as Files.Read and Files.Read.Selected are not available as application permissions and therefore cannot be used by a background synchronisation service.
With the Sites.Selected permission it is only possible to list the drives (drive ids) and files (file ids) within those sites that have been allowed by the Sites.Selected permission.
The Microsoft Graph API requires both a drive id and a file id in order to fetch metadata or file contents. With these permissions alone, it would not be possible to discover drives or files beyond those specified by the Sites.Selected permission. Therefore, by proxy, the Files.Read.All permission used along site Sites.Selected means that the application registration can only access files within the sites allowed by the Sites.Selected permission.
Legacy authentication (Client Secret – deprecated)
Client secret authentication is deprecated and should not be used for new SharePoint Online Workplace Search connectors.
This section is provided for reference only to support existing integrations and migration scenarios. We strongly recommend using certificate-based authentication for all new connectors.
In your Azure App registration:
- Navigate to Client credentials: Certificates & Secrets.
- Select New client secret
- Pick a name for your client secret and select an expiration date.
- note: after this expiration date, you will have to reconfigure your connector credentials by following these steps again
- Note the client secret Secret ID.
- Note the client secret Secret Value (you must do this immediately before leaving the page).
After creating the client secret, enter the Secret ID and Secret Value into the SharePoint Online connector credentials configuration.
SharePoint Configuration
The Azure OAth App does not automatically have access to the SharePoint REST API, so the additional step is also required.
Refer to the following documentation for setting SharePoint permissions.
- To set DisableCustomAppAuthentication to false, connect to SharePoint using PowerShell and run
set-spotenant -DisableCustomAppAuthentication $false - To assign full permissions to the tenant in SharePoint Online, go to the Manage App Permissions page within SharePoint.
- The URL follows this pattern:
https://<office_365_tenant_URL>-admin/_layouts/15/appinv.aspx. For example, if your SharePoint URL is https://contoso.sharepoint.com, then you should go to https://contoso-admin.sharepoint.com/_layouts/15/appinv.aspx.
- The URL follows this pattern:
- This loads the SharePoint admin centre page, where you can create the app permissions request.
- In the App ID box, enter the application ID that you recorded earlier, and then click Lookup. The application name will appear in the Title box.
- In the App Domain box, type
<tenant_name>.onmicrosoft.com- where<tenant_name>should be replaced by your tenant name (e.g.contoso.onmicrosoft.com) - In the App’s Permission Request XML box, type the following XML string:
<AppPermissionRequests AllowAppOnlyPolicy="true">
<AppPermissionRequest Scope="http://sharepoint/content/tenant" Right="FullControl" />
<AppPermissionRequest Scope="http://sharepoint/social/tenant" Right="Read" />
</AppPermissionRequests>
Please ensure that the above xml is applied exactly as specified (with line breaks) otherwise the permissions may not apply correctly
Troubleshooting
"Insufficient privileges to complete the operation."
If you see the "Insufficient privileges to complete the operation." error message, then ensure that the relevant API permissions (Graph, SharePoint) have been set.
"Attempted to perform an unauthorized operation"
If you see the following in your workplace search logs:
Error | Value of parsed object was null. Serialised value: "{"odata.error":{"code":"-2147024891, System.UnauthorizedAccessException","message":{"lang":"en-US","value":"Attempted to perform an unauthorized operation."}}}"
Then this normally means that the SharePoint Configuration has not been applied correctly. Ensure that the above SharePoint Configuration steps have been followed correctly, and that the steps were performed on the SharePoint Admin site (-admin suffix).
"Microsoft.IdentityModel.Tokens.AudienceUriValidationFailedException"
if you see the following error in your workplace search logs:
Error | Failed to process serialised response. Serialised value: "{"error_description":"Exception of type 'Microsoft.IdentityModel.Tokens.AudienceUriValidationFailedException' was thrown."}"
This can be a result of not setting the TenantName parameter in the SharePoint Online connector credentials JSON correctly. For example, if your tenant is contoso.onmicrosoft.com, then you would enter contoso. So, it should look like:
{
"ApplicationClientId": "[Your ApplicationClientId]",
"DirectoryTenantId": "[Your DirectoryTenantId]",
"SecretId": "[Your SecretId]",
"SecretValue": "[Your SecretValue]",
"TenantName": "contoso"
}This could also mean that the SharePoint Configuration has not been applied correctly. Ensure that the above SharePoint Configuration steps have been followed correctly, and that the steps were performed on the SharePoint Admin site (-admin suffix).
Updated about 1 month ago
