Azure AD Connector
To proceed you will need to have access to both Interacts Application Settings and the Azure Active Directory portal simultaneously.
First, we will register your Interact instance as an application within Azure. You will need take note of the following values. They will be needed for configuring Azure AD as a profile source within Interact later:
- Application ID
- Directory ID
- Client Secret
- Azure domain name
Configure Azure
1. Register a new app
From within your Azure Portal: Select Azure Active Directory from the left-hand menu. Next select App registration and New registration from the subsequent sub-menus.
Note: Do not choose the “App Registration (Legacy)” option. For legacy configurationClick here
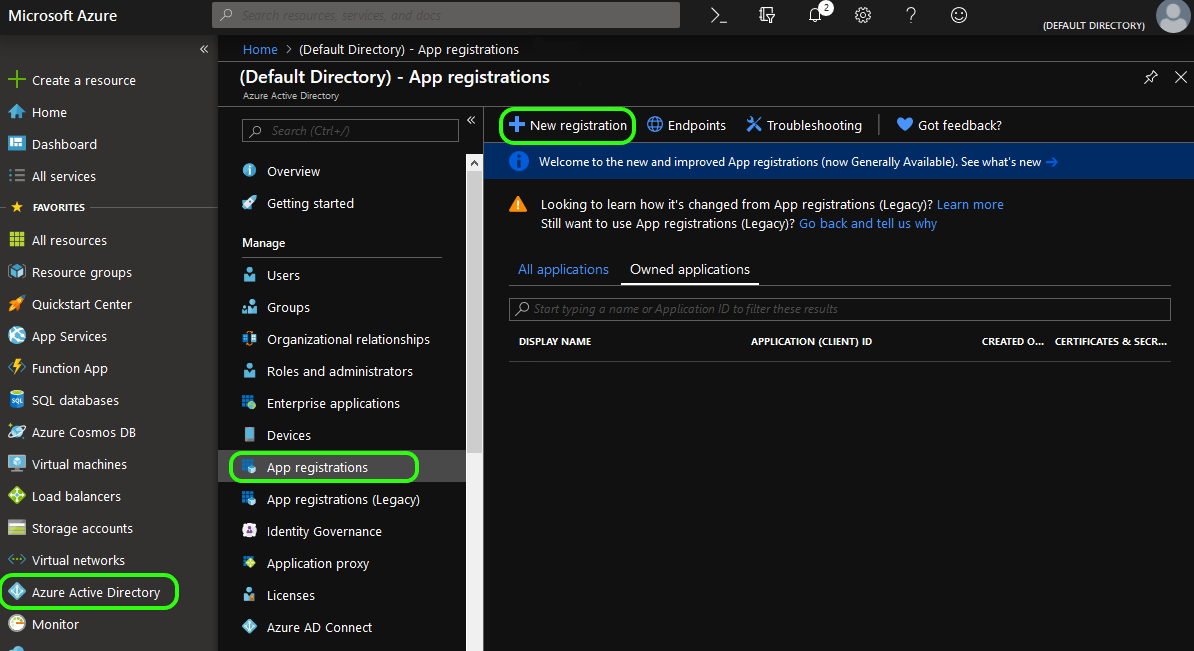
From here you will be presented with a form titled Register an application.
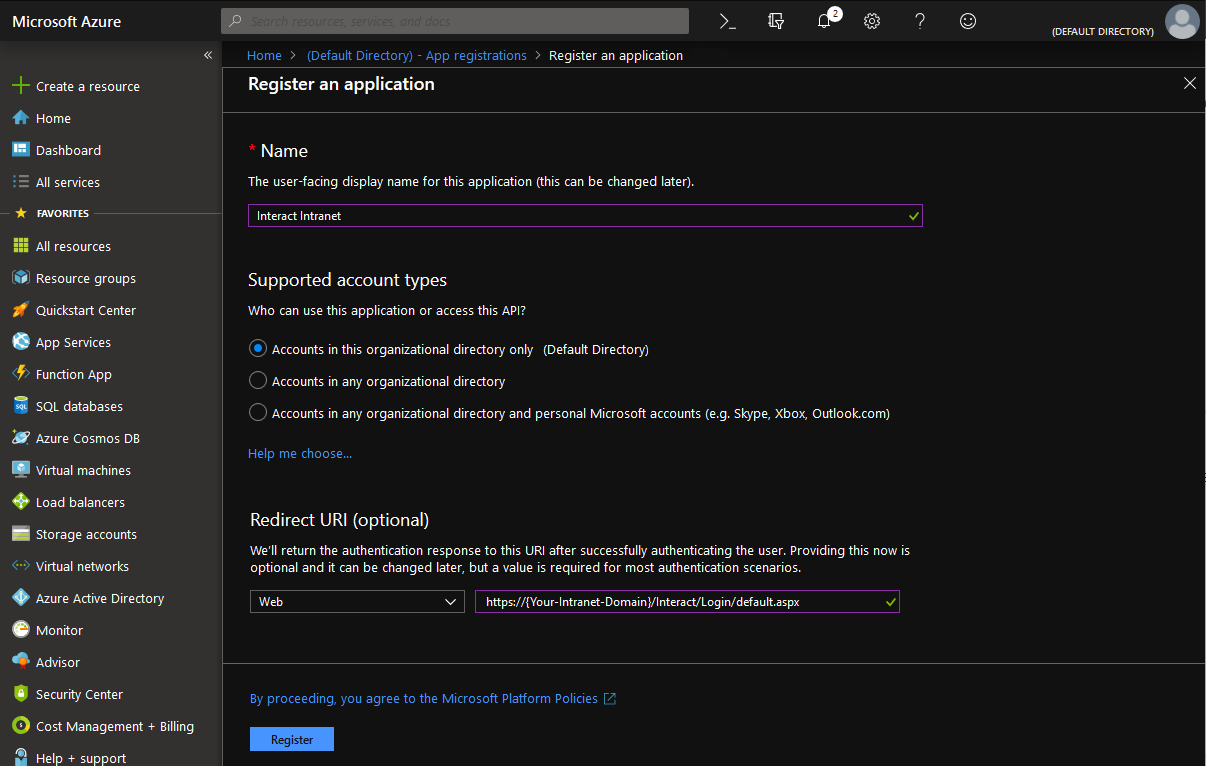
Give the application registration a name, set the supported account type to organizational directory only and fill out the Redirect URI
Redirect URI'sYour Redirect URI will always match the following pattern:
https://{Your-Intranet-Domain}/Interact/Login/default.aspx
Click Register to continue.
2. Add a new client secret
From the sub-menu select Certificates & secrets and then New client secret
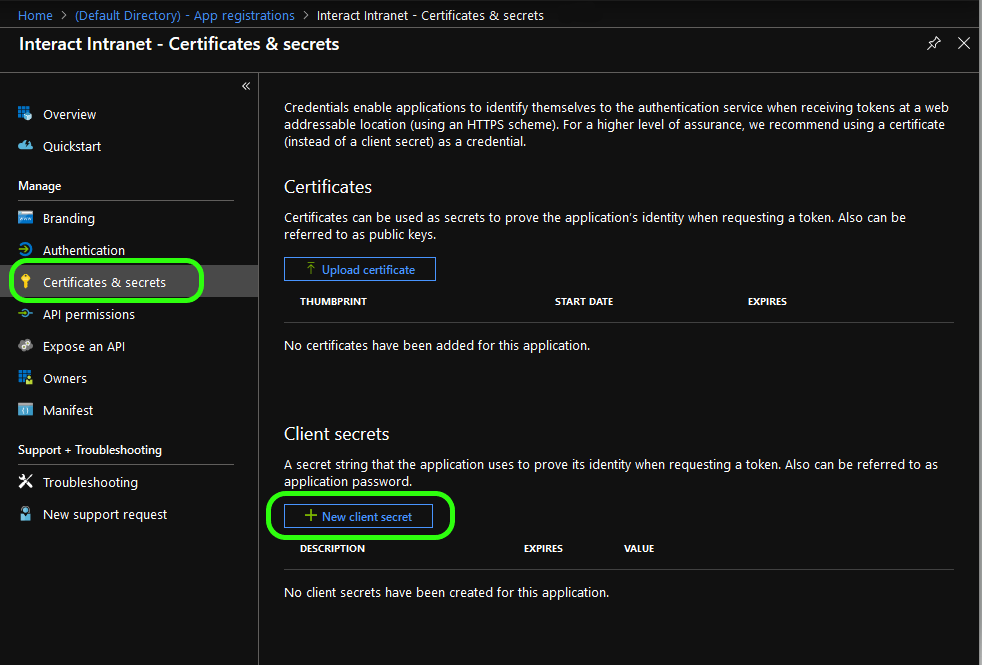
Give the client secret a name and select how long you want it to be valid, then click Add
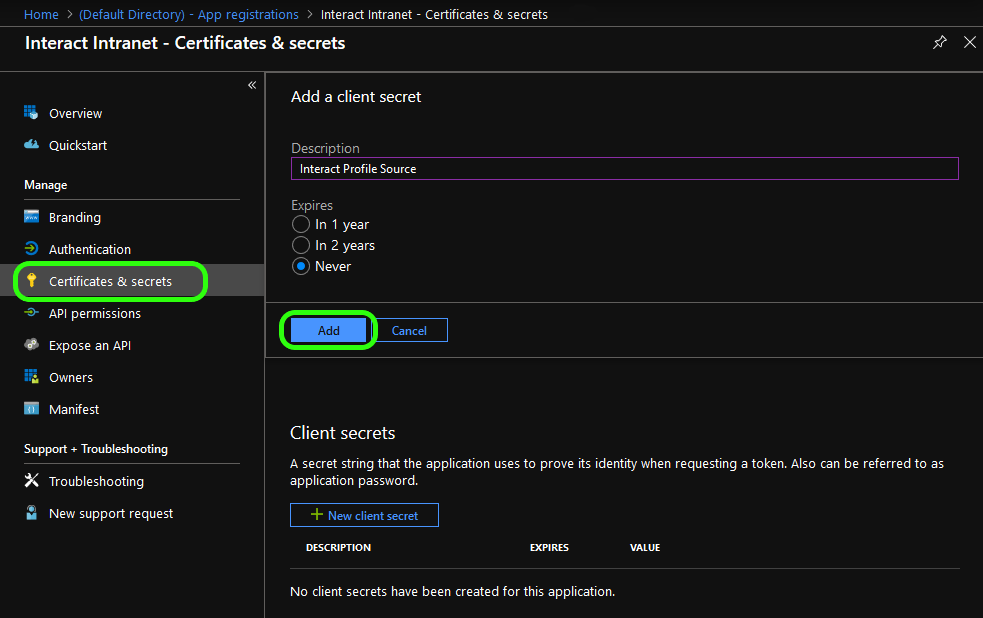
The new client secret will appear at the bottom of this window. Make a note of it because it won’t remain visible.
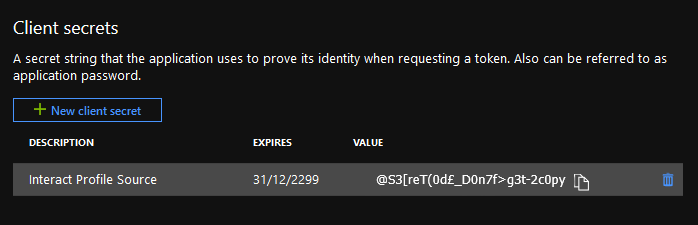
3. Add permissions
Next, select API permissions from the side menu and then Add permission
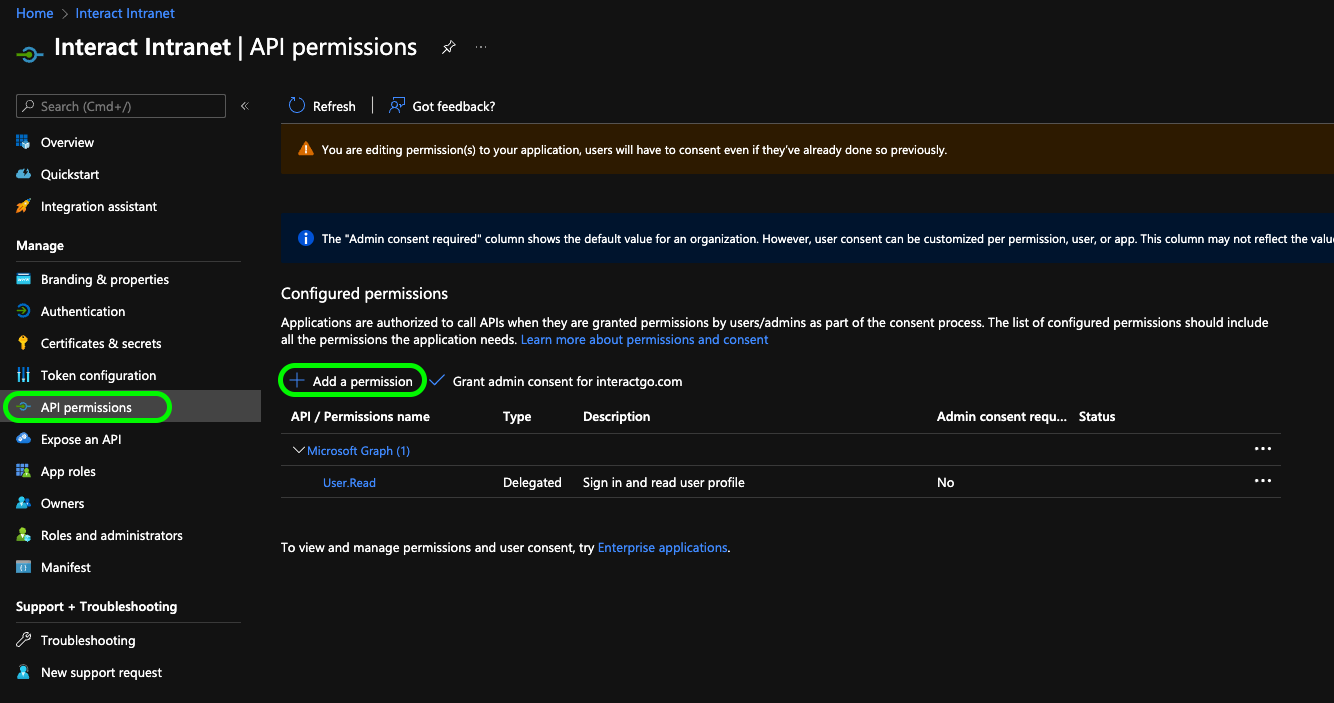
You will be presented with a Request API permissions pane. From the Microsoft APIs tab and select Microsoft Graph.
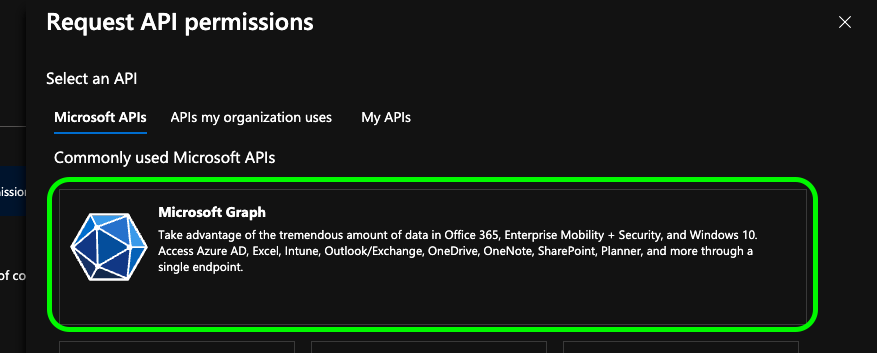
Select Delegate permissions. From the exposed options expand Directory and select Directory.Read.All also expand User and select User.Read
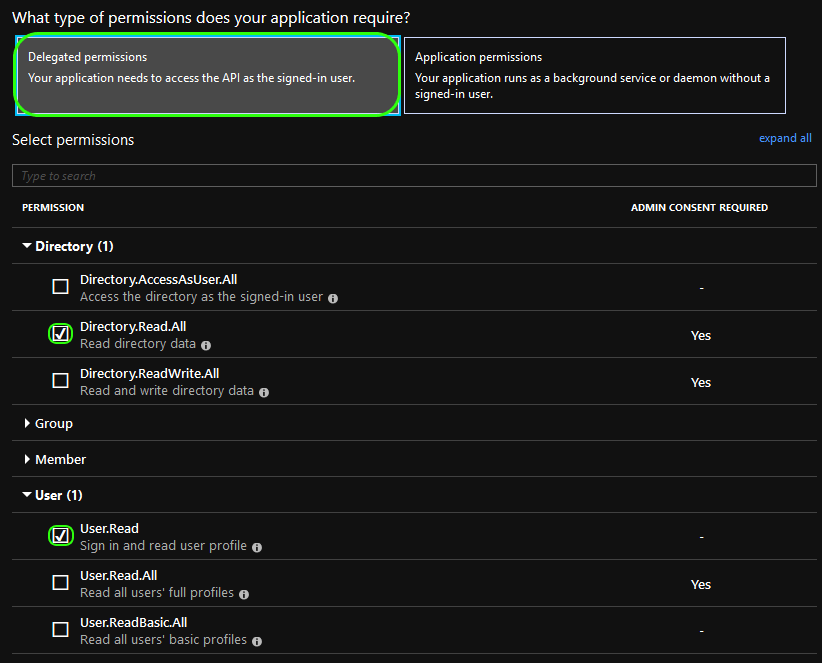
Next, select Application permissions. Expand Directory and select Directory.Read.All
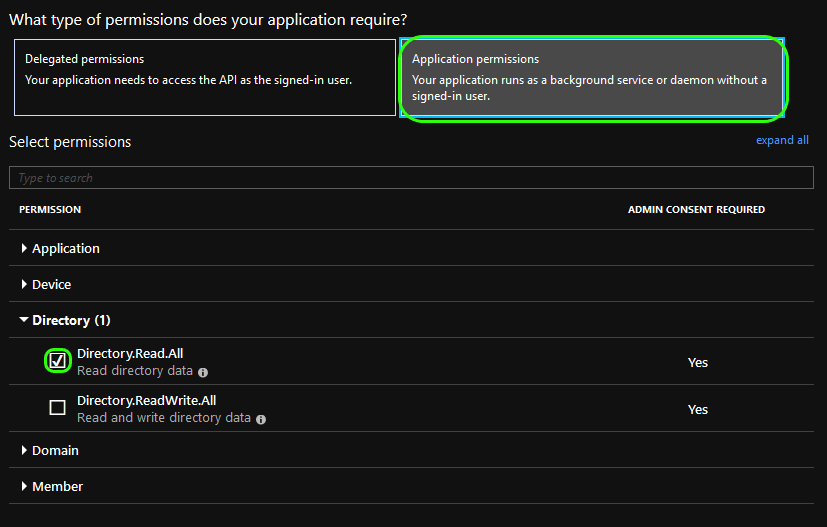
At the bottom of the window click Add permission to close.
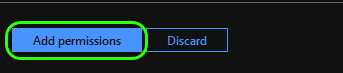
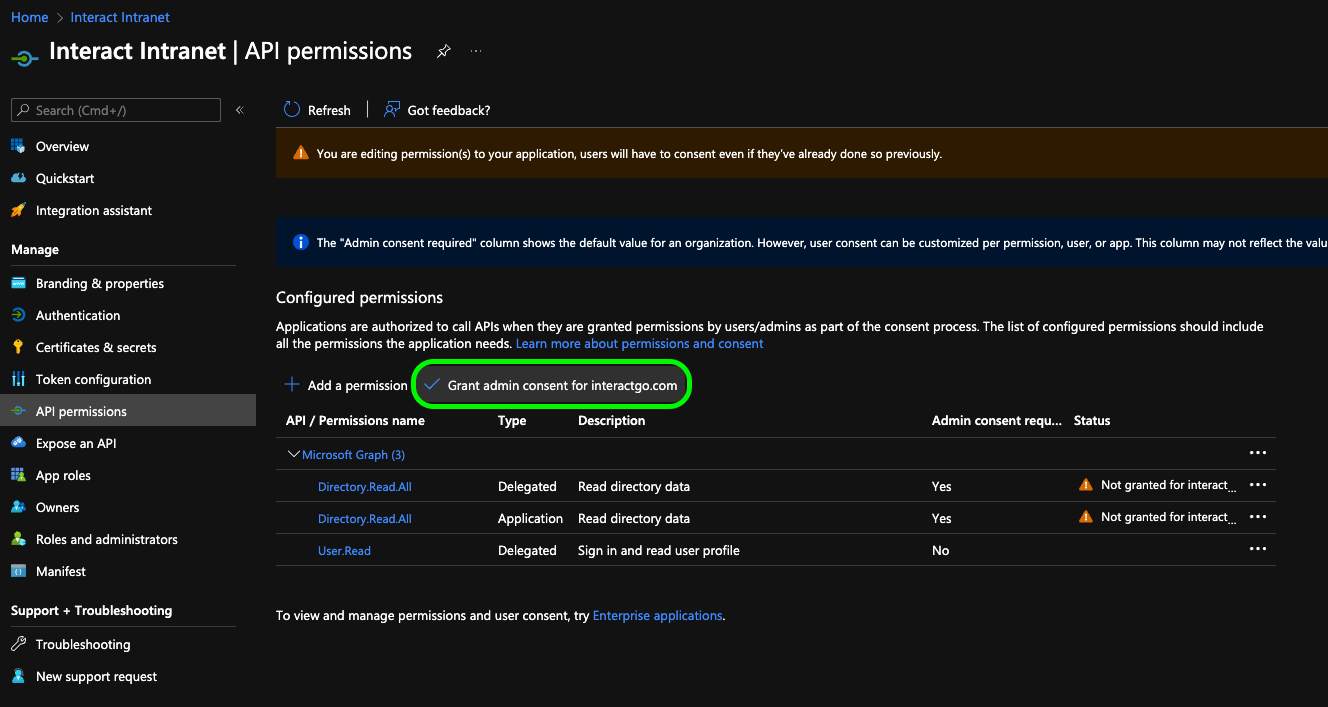
4. Grant Permissions
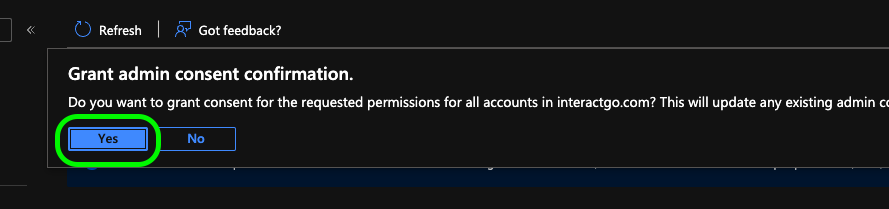
You will now be presented with a list of your selected permissions. Click the Grant admin consent button to apply these options.
Click Yes to confirm
5. Obtain EntityID
Next, log into your Interact intranet and navigate to Application Settings > Control Panel > Manage Security > Manage SAML Authentication.
If your domain isn’t currently setup click Setup Domain, otherwise skip 2 steps.
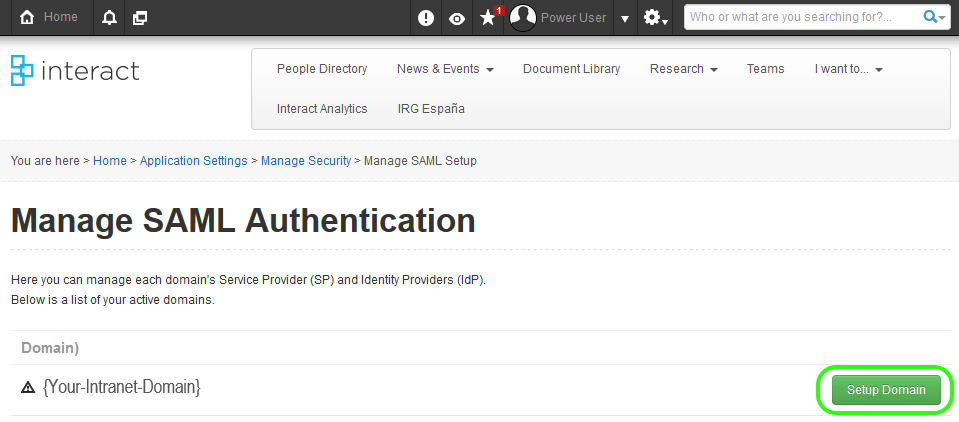
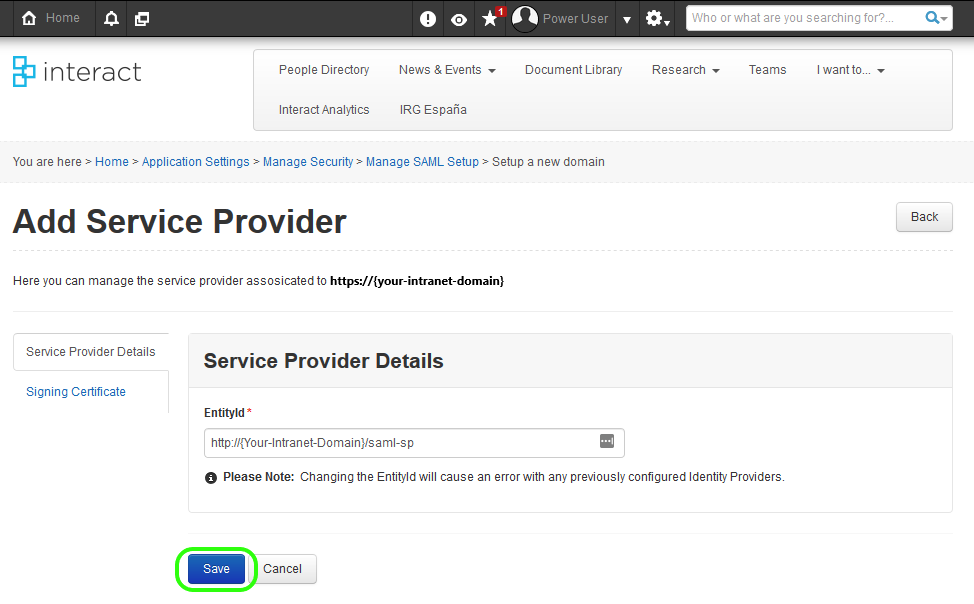
On the next page click Save
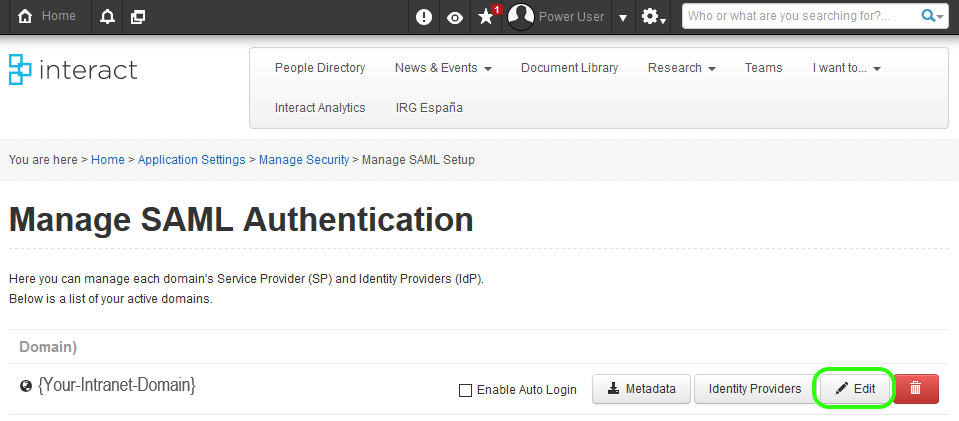
Click the Edit button for the domain you are working against.
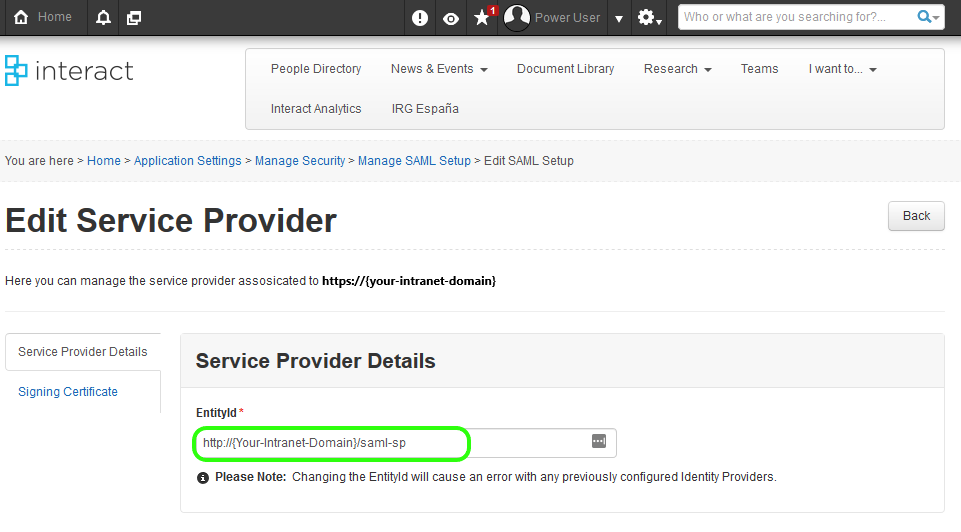
On the next screen copy the text of the EntityId.
Switch back to your Azure Portal. From the side sub-menu click Expose an API and then, from the main pane, click Set to set the Application ID URI
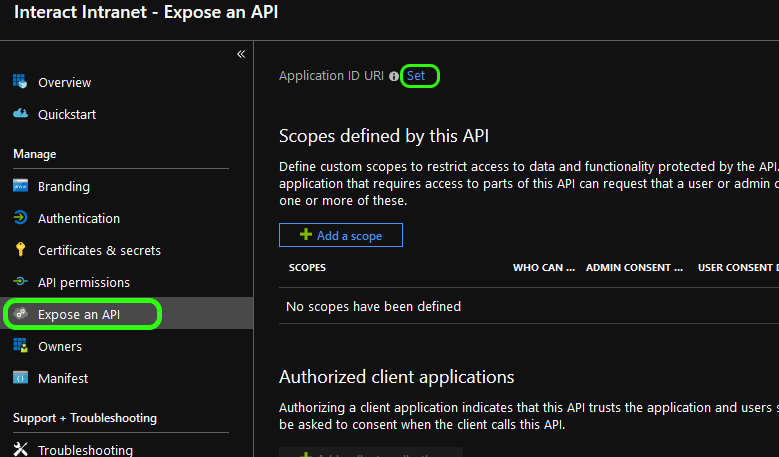
Paste the EntityId, copied from your Interact settings, into the Application ID URI.
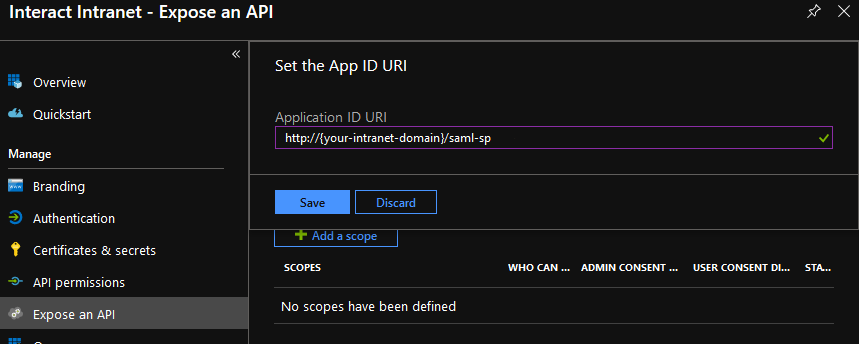
Click Save
6. Collect required ID's
That is the Azure configuration completed. Before going forwards you will need:
- The Secret you created in Step 2
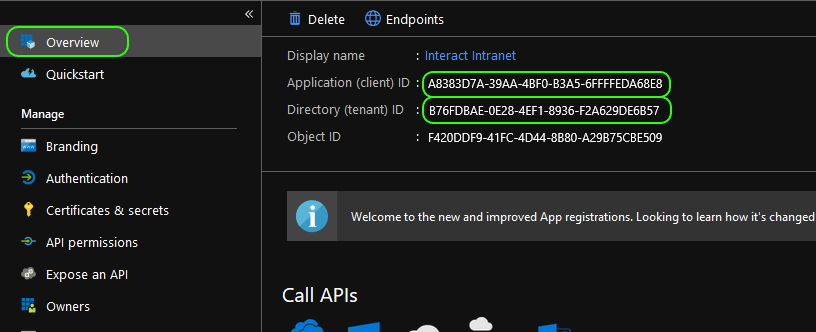
- The Application ID and Directory ID, these can be found by clicking Overview from the side menu.
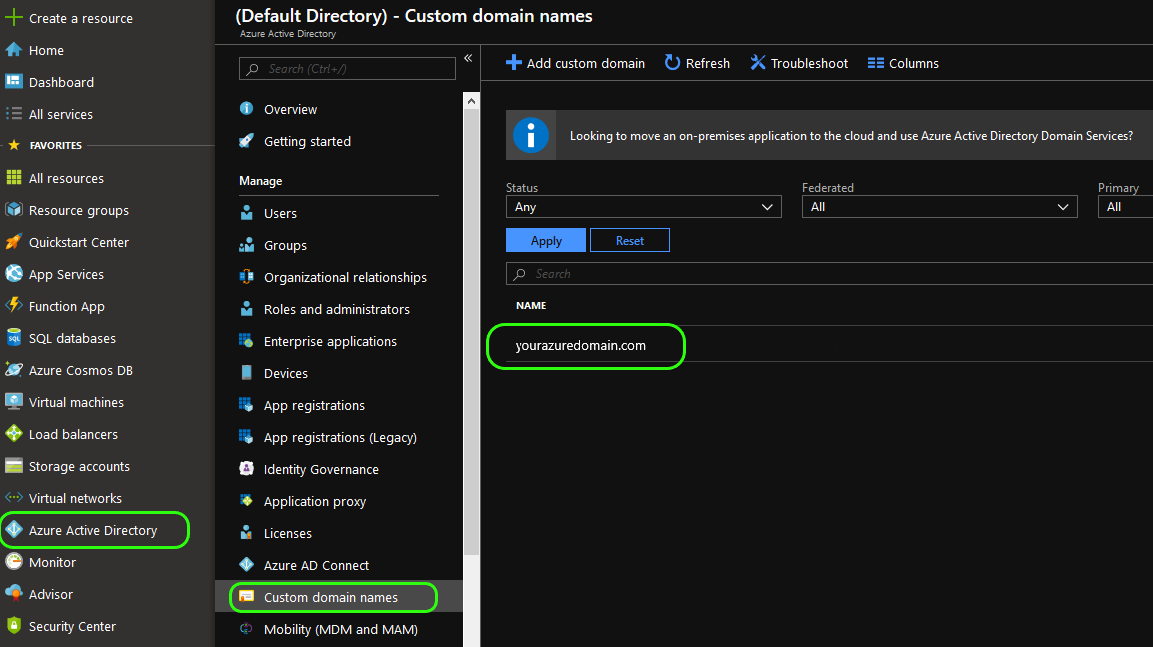
You will also need your azure domain name, this can be found by clicking Azure Active Directory from the main side menu, then Custom domain names from the sub-menu. Your domain name will be in the pane to the right.
Configure Interact
1. Add a profile source
From Interact, navigate to Application Settings > Manage People > Manage Profile Sources
From here you should see an option for Microsoft Azure, if not, please contact the service desk.
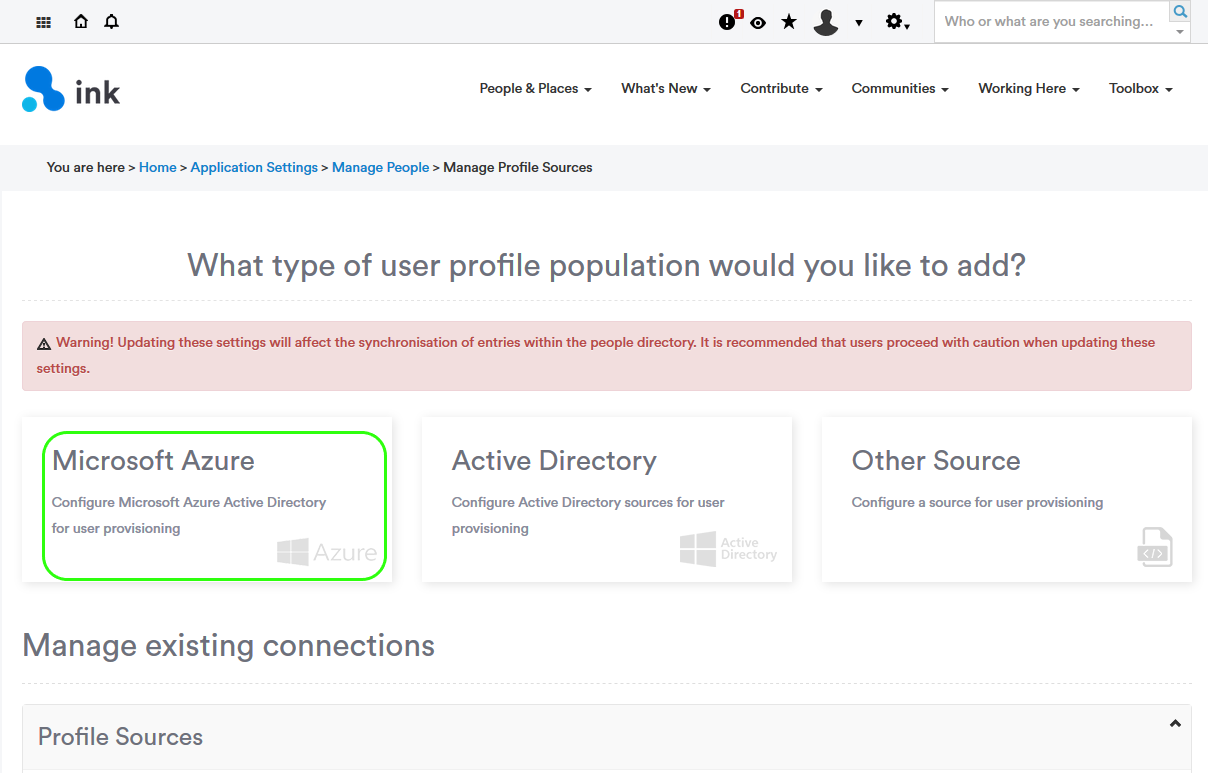
Note: This window may look different depending on any customizations made to your instance.
Click Microsoft Azure
2. Enter the ID's from Azure
Enter the Application Id, Secret and Directory Id you have copied from the Azure configuration.
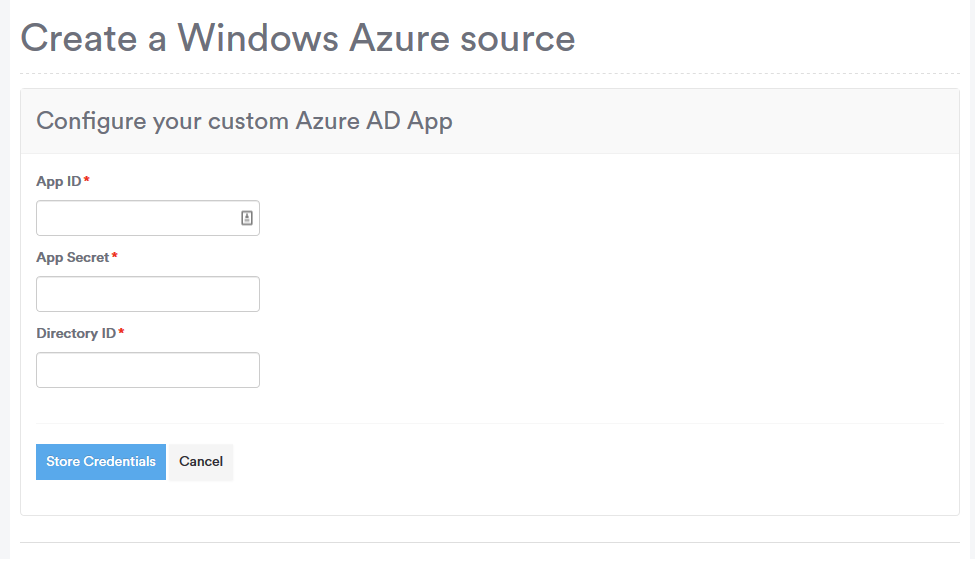
Click Store Credentials
3. Enter Domain Details
Next, enter your Azure Domain and the Name you want to give the SAML configuration.
Only fields marked with an <b style="color:red;">\*</b> are required.
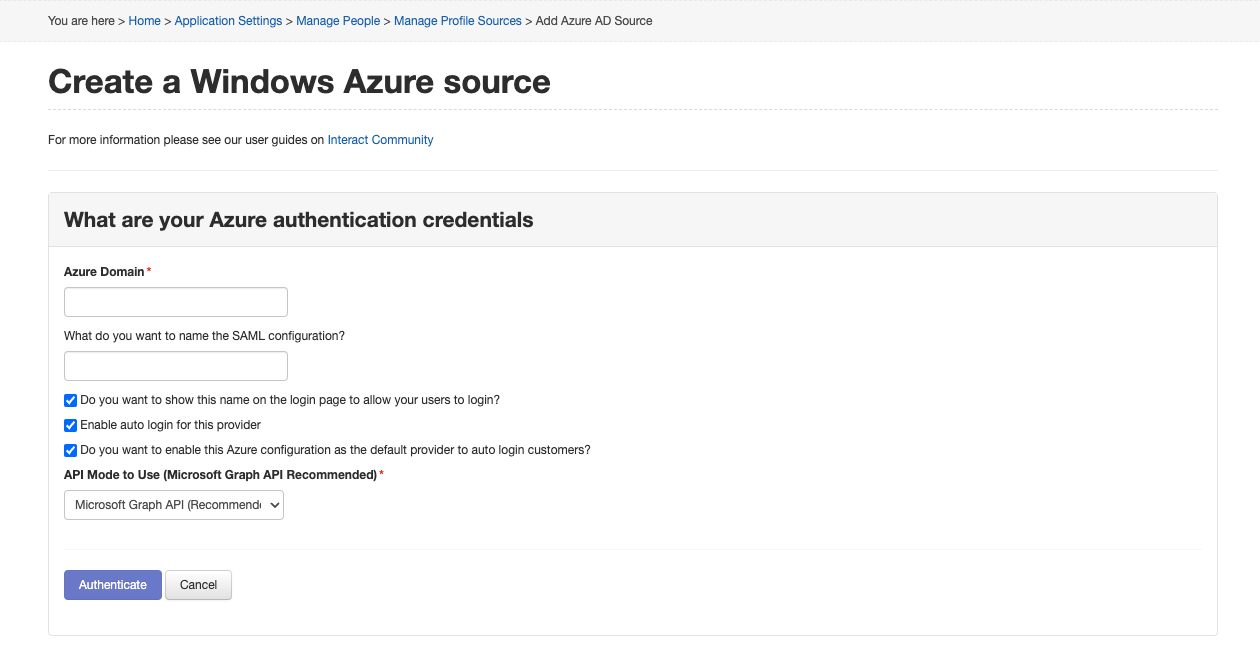
What do you want to name the SAML configuration? - this field is used when within the SAML configuration area within Interact, and is seen if the 'Show provider on login screen' is checked. In the example below I have named this 'MG azure'.
Do you want to show this name on the login page to allow your users to log in? - This option will show the name above to users if using the login page within Interact.
Enable auto login for this provider - this option sets the Azure configuration being set up to be used to auto log users in, if this option is enabled at this stage users wanting to log in to the intranet must be within Azure. It is recommended that this option remains unchecked until the Azure setup is completed.
Do you want to enable this Azure configuration as the default provider to auto login users? - this option replaces any pre-configured SAML configurations with this Azure configuration as the default when navigating to the login domain this domain will be used. This can be altered by accessing the SAML configuration screens.
API Mode to Use
Leave the API Mode set to Microsoft Graph API.
Azure AD Graph API is available only for legacy configurations and is being deprecated in June 2020. All profile sources should be migrated to Microsoft Graph API by June 2020 to avoid disruption.
Click Authenticate once completed.
4. Configure field mappings
Once authenticated you can select how to map fields from Azure to fields in Interact. All defaults are set within the dropdown fields however this can be updated to match your configuration in Azure. Fields which aren't required for synchronization can be marked as 'Do not map' this will ignore any field set within Azure.
Note: Additional FieldsYou may find that some fields are missing here that you have in Azure and want to synchronize in to Interact. Let us know by raising a request within the Product Enhancement forum and we'll be able to investigate this as an iteration on this functionality. Currently, it's not possible to use any other fields than the fields listed below, this includes Azure's Additional fields*
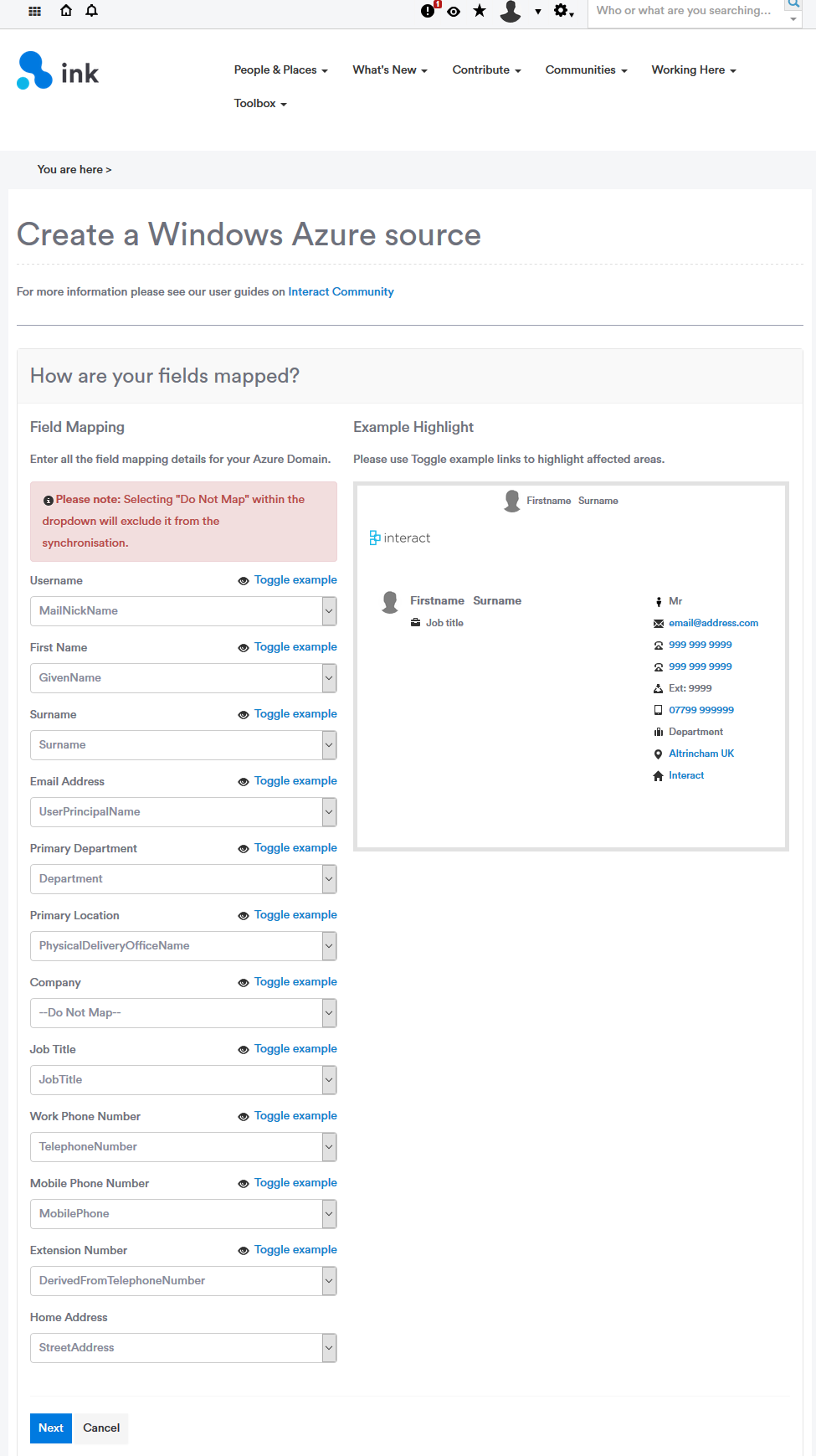
Once complete, click Next
5. Configure sync options
Select which options you would like to sync from Azure to Interact. Below you can choose which default values to use if one isn't supplied for a user within Azure.
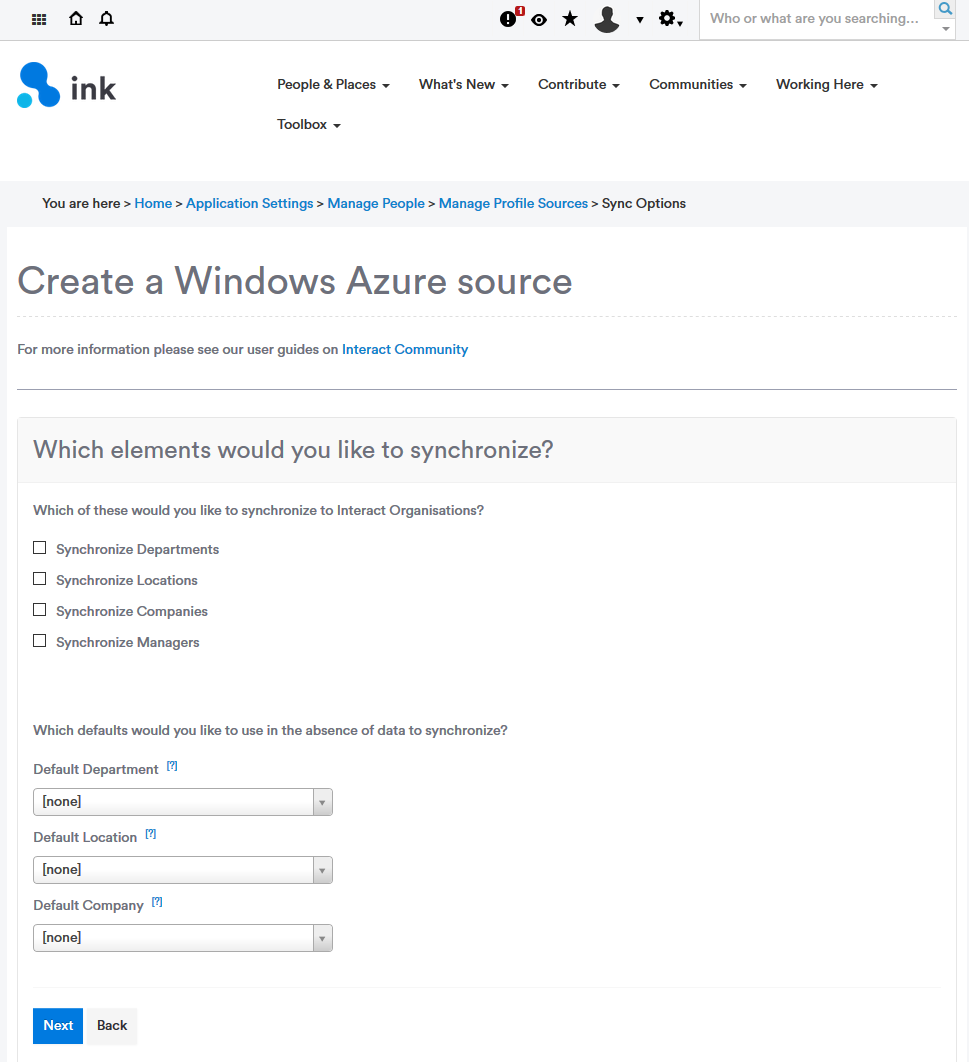
Click Next
6. Define missing user options
Select how Interact should handle users which are no longer in Azure AD or have their accounts set to inactive within Azure AD
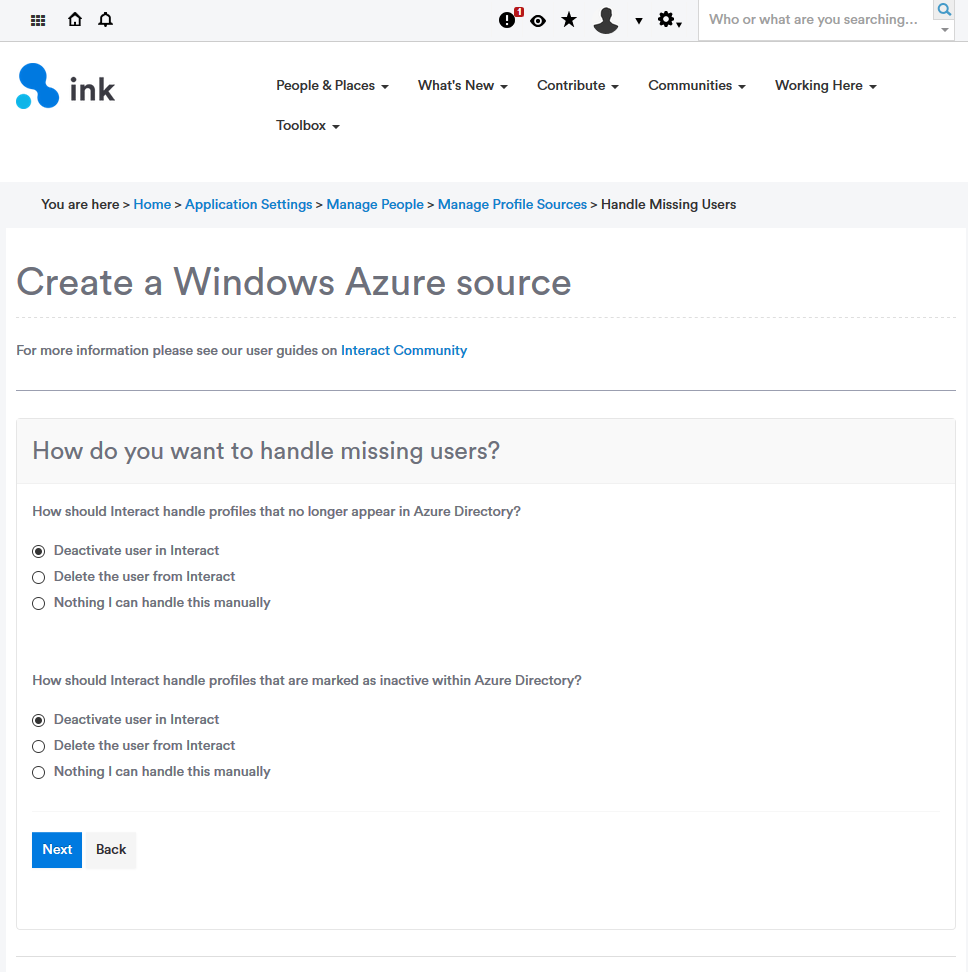
Click Next
7. Select group(s)
Select which security groups of users you would like to sync into Interact. Users must exist within at least one security group to be synced to your site (distribution groups cannot be targeted for sync).
Note: Group SearchWhen using the search feature, groups with 0 users will not appear in the results.
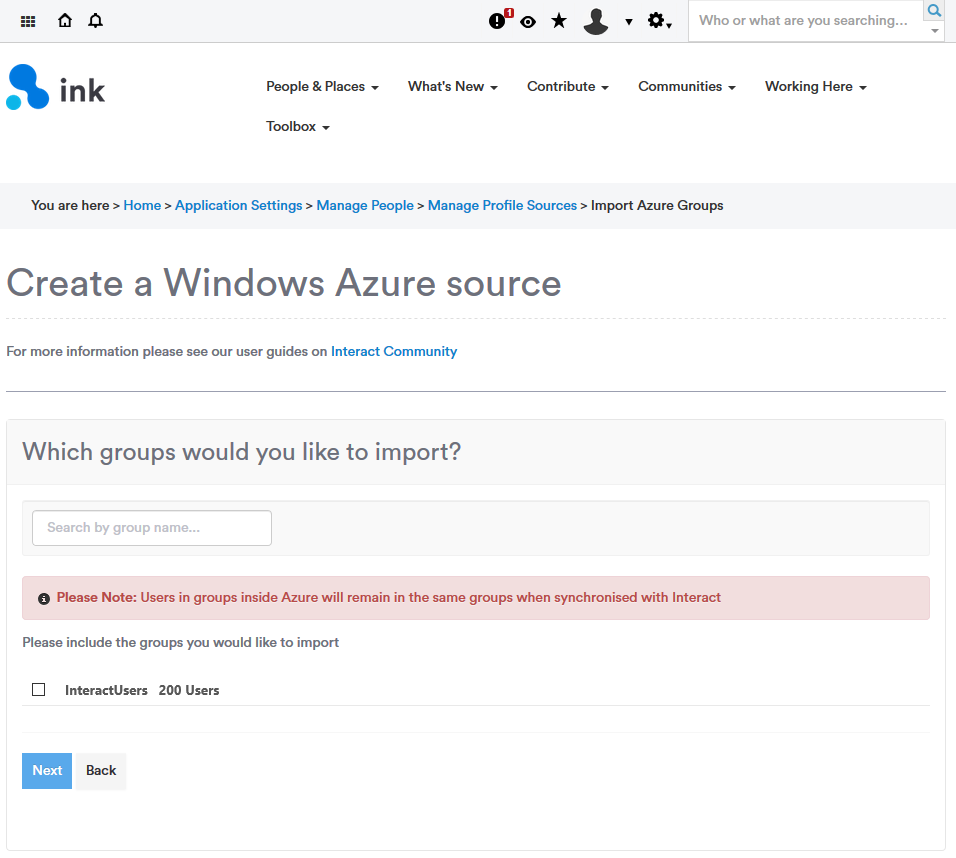
Click Next
8. Schedule the sync
Set the frequency you would like to pull your user profile data.
Note: Scheduled TimeThe scheduled time must be saved in UTC 24h format.
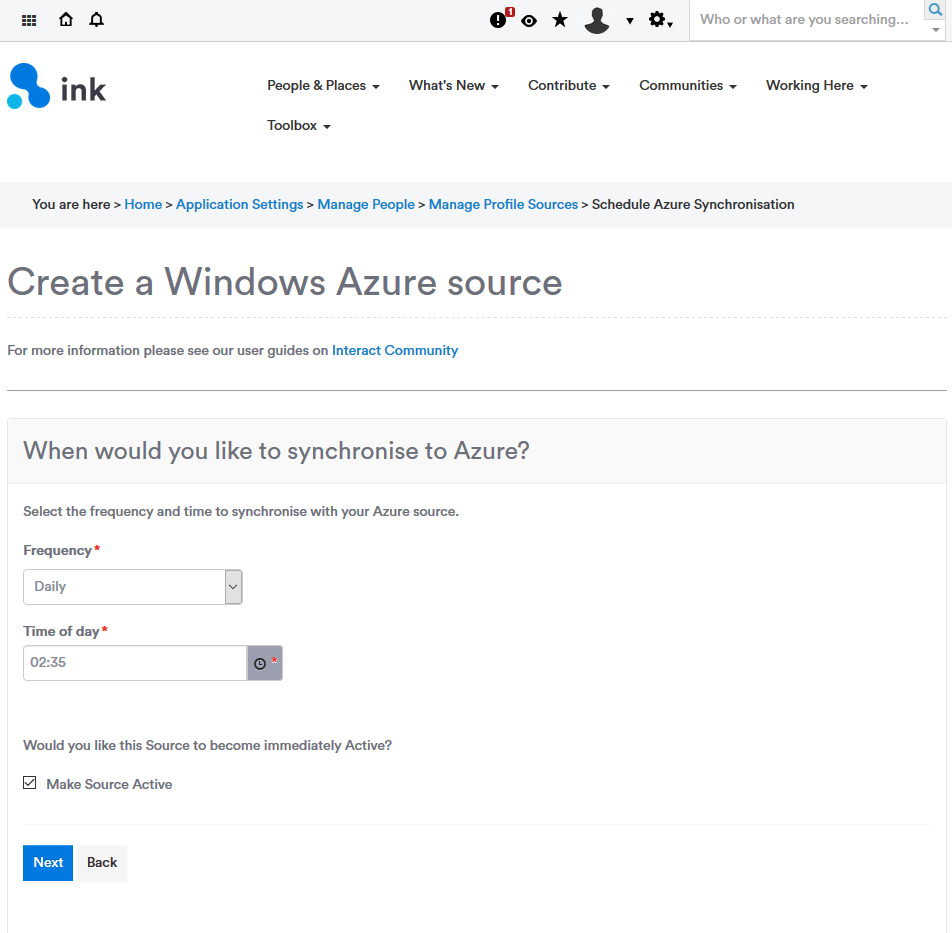
If you are ready to make this profile source active now, then click Make Source Active. This can be changed later.
Click Next.
9. Review configuration
Next, review your configuration and then Click Save. If there is anything you need to change you can click Back.
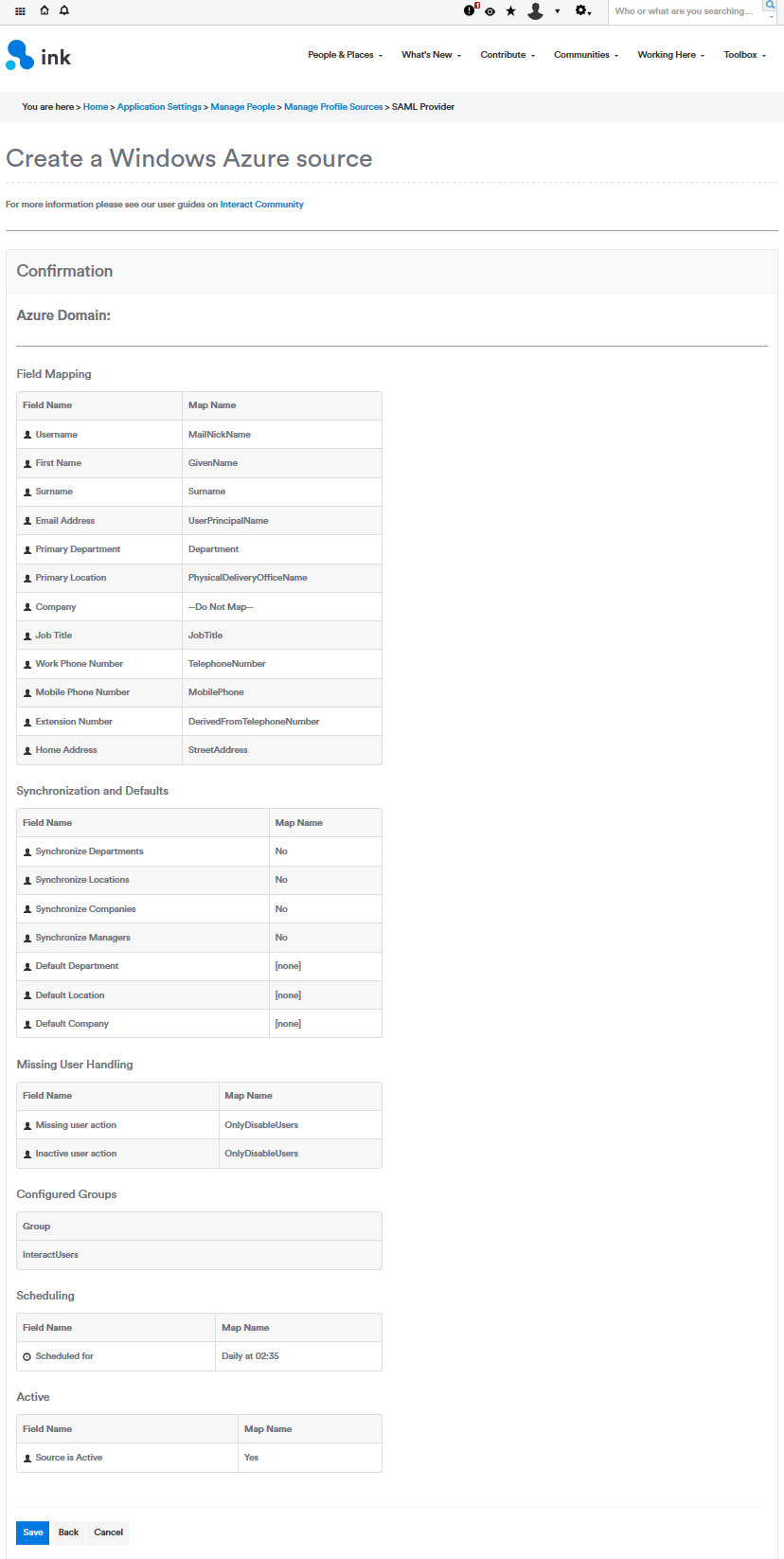
Finished
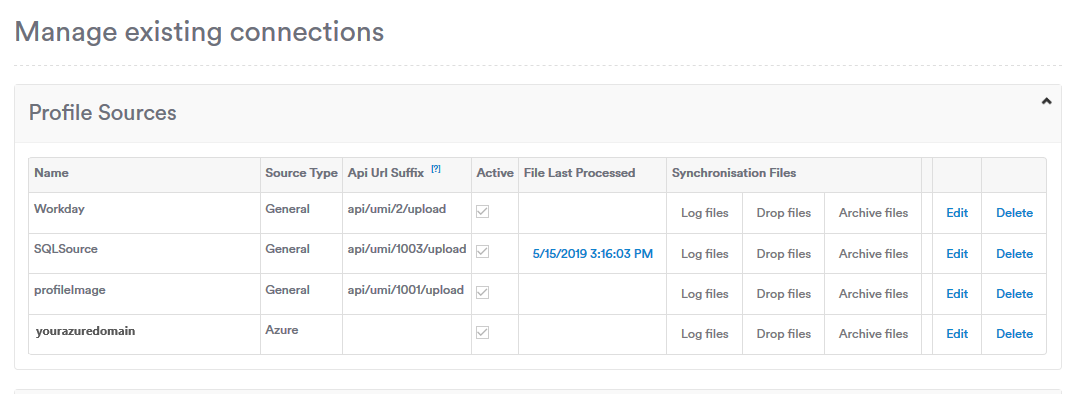
Your Azure profile source is now configured. It will appear under the list of existing profile sources.
Edit an existing Profile Source
You can edit the Azure configuration by navigating to Application Settings > Manager People > Manage Profile Sources, then clicking on the "Edit" button of whichever source you would like to adjust.
Updated 9 months ago
