With Azure AD (Authentication Only)
To proceed you will need to have access to both Interact's Application Settings and the Azure Active Directory portal simultaneously.
First, we will register your Interact instance as an application within Azure.
Configure Azure
1. Register a new app
From within your Azure Portal: Select Azure Active Directory from the left-hand menu. Next select App registration and New registration from the subsequent sub-menus.
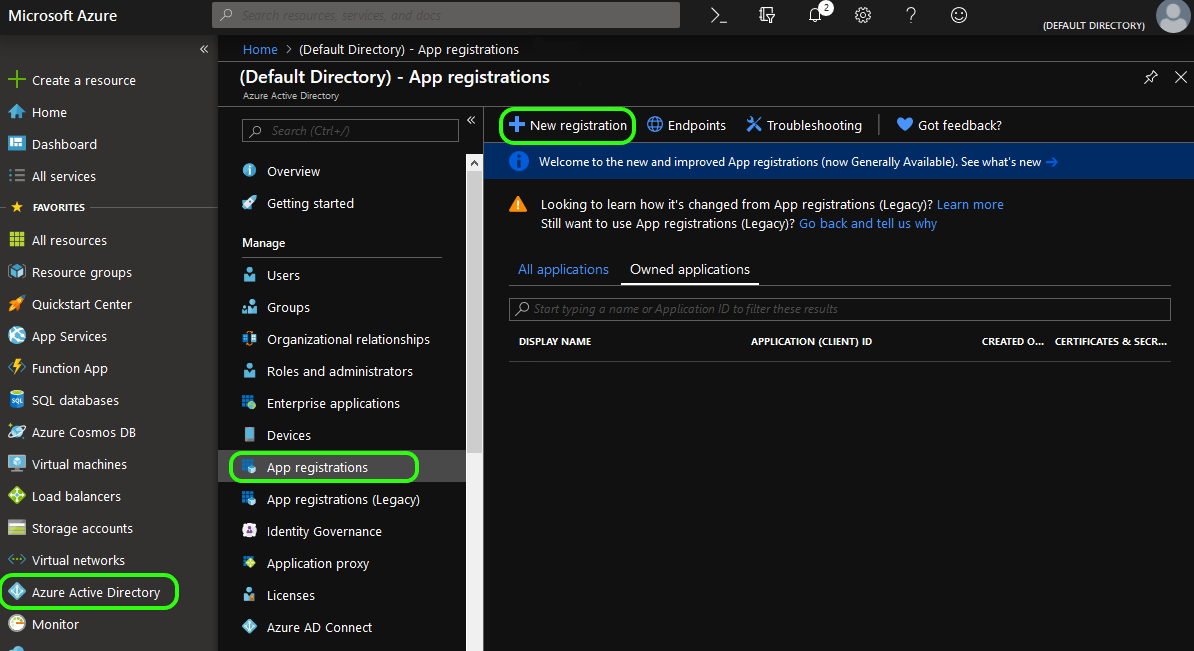
From here you will be presented with a form titled Register an application.
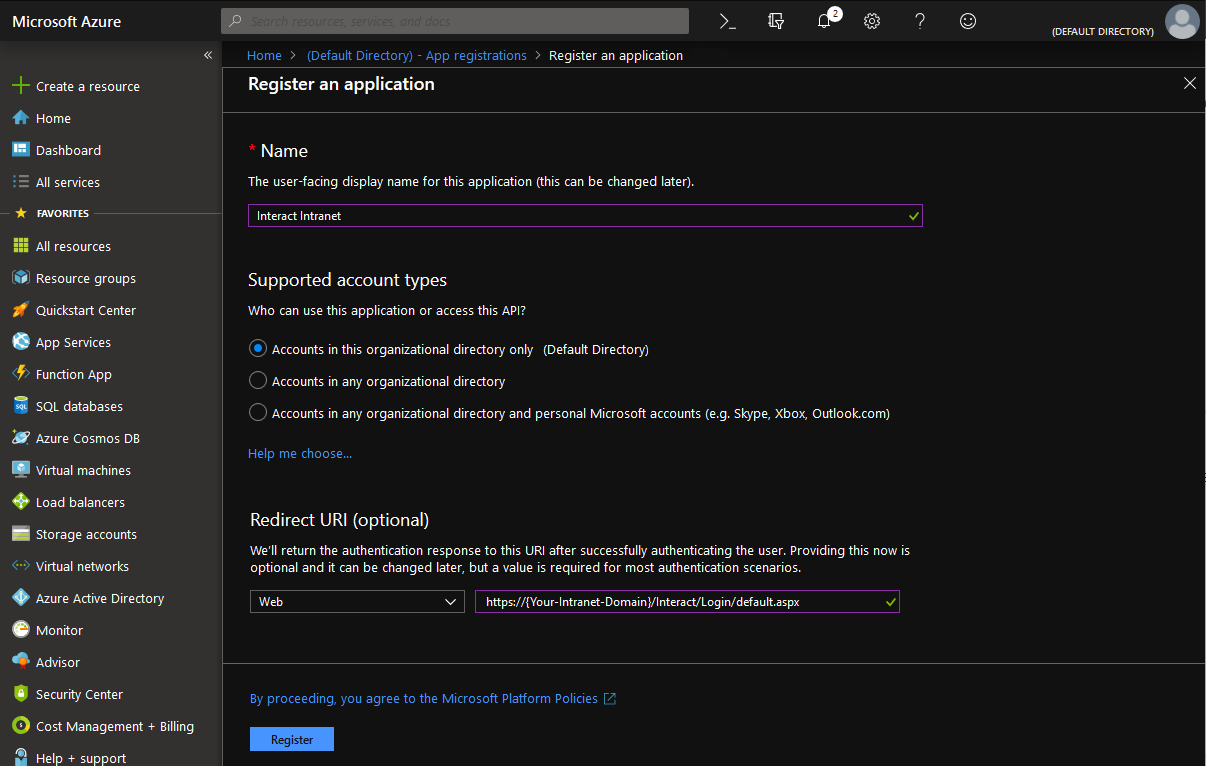
Give the application registration a name, set the supported account type to organizational directory only and fill out the Redirect URI: https://{Your-Intranet-Domain}/Interact/Login/default.aspx
Click Register to continue.
2. Add permissions
Next, select API permissions from the side menu and then Add permission
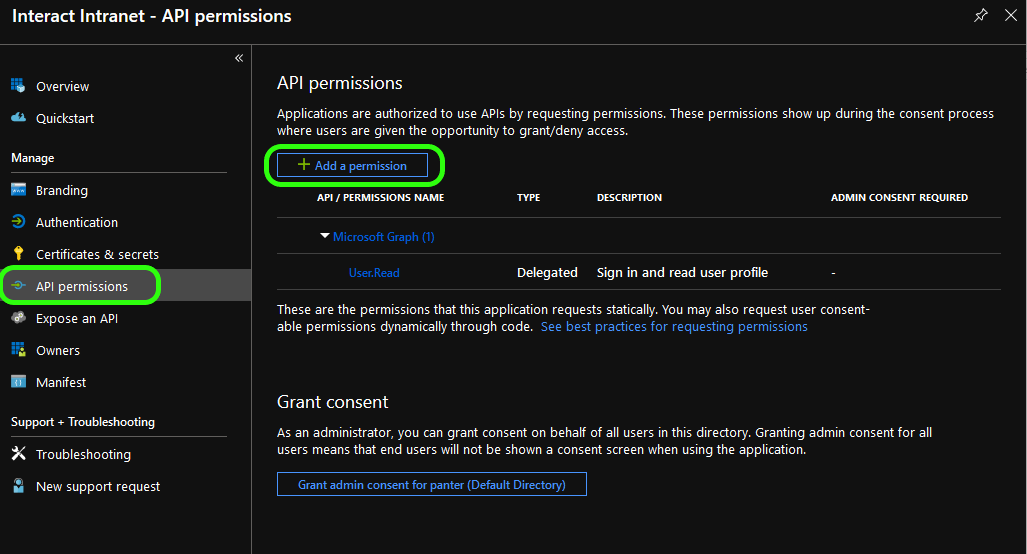
You will be presented with a Request API permissions pane. From the Microsoft APIs tab choose Microsoft Graph.
Select Delegate permissions. From the exposed options expand Directory and select Directory.Read.All and DirectoryAcessAsUser.All. Also expand User and select User.Read
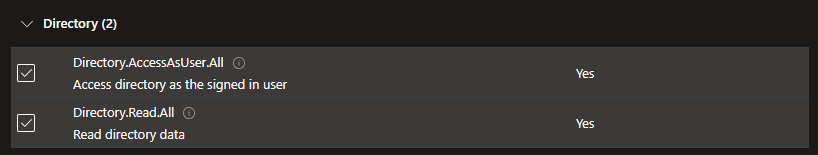
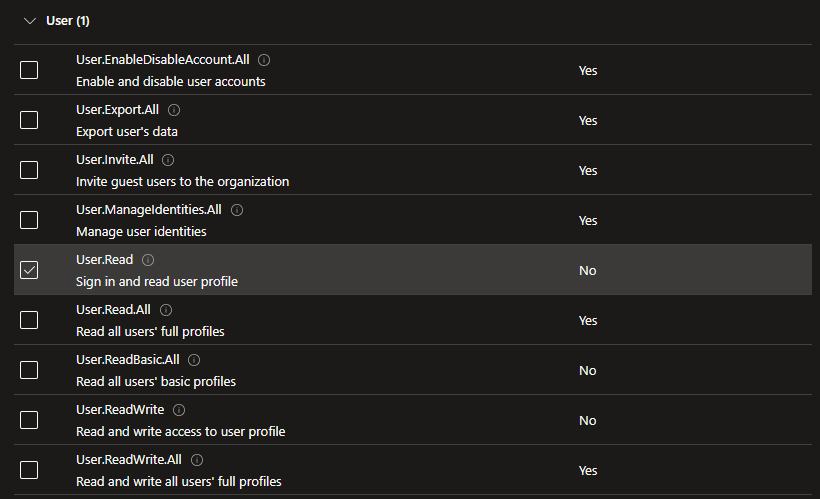
At the bottom of the window click Add permission to close.
3. Grant Permissions
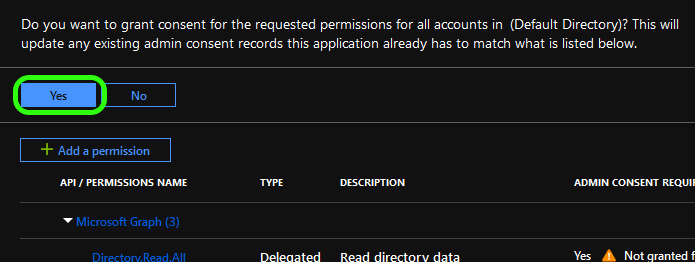
You will now be presented with a list of your selected permissions. Click the Grant admin consent button to apply these options.
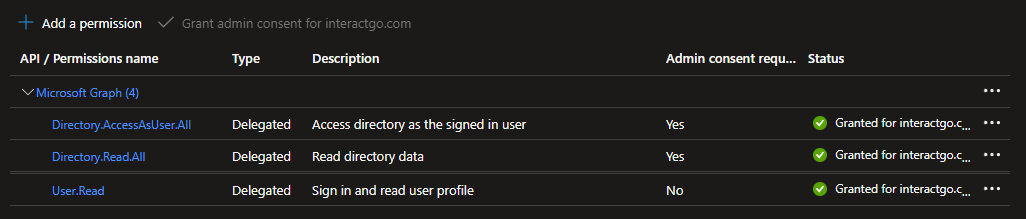
Click Yes to confirm
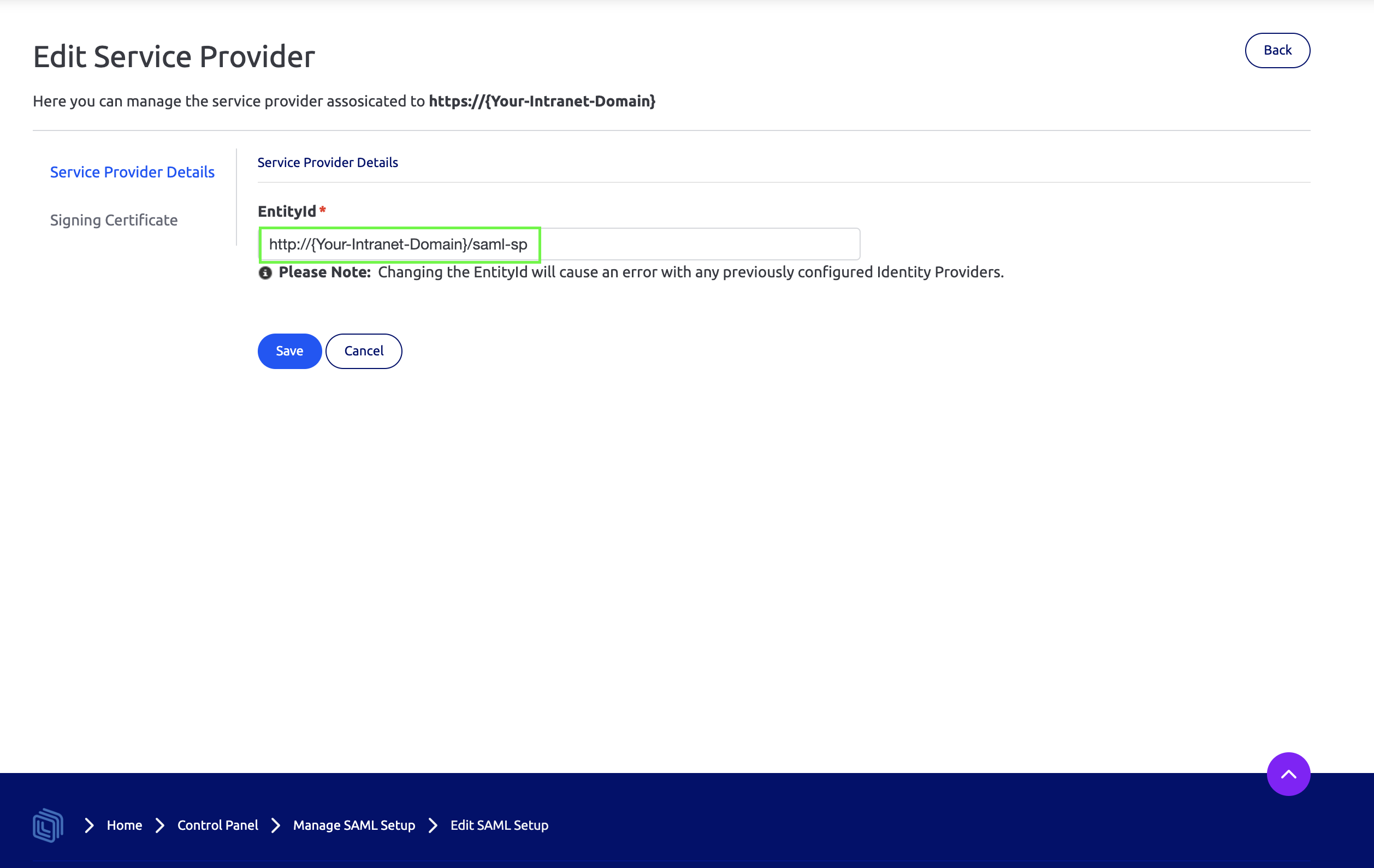
4. Obtain EntityID
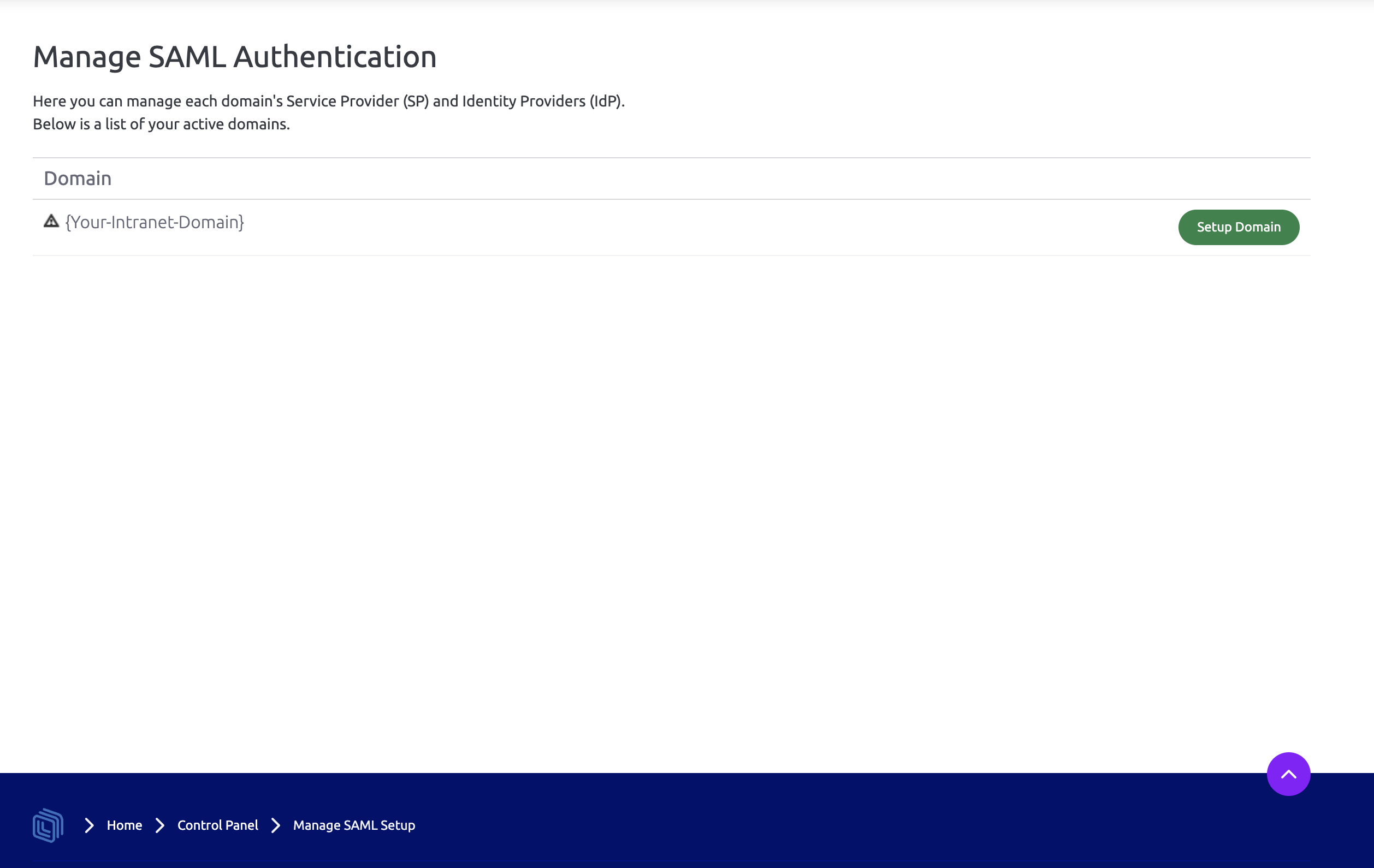
Next, log into your Interact intranet and navigate to Control Panel > Manage Security > SAML Authentication .
If your domain isn’t currently setup click Setup Domain, otherwise, skip 2 steps.
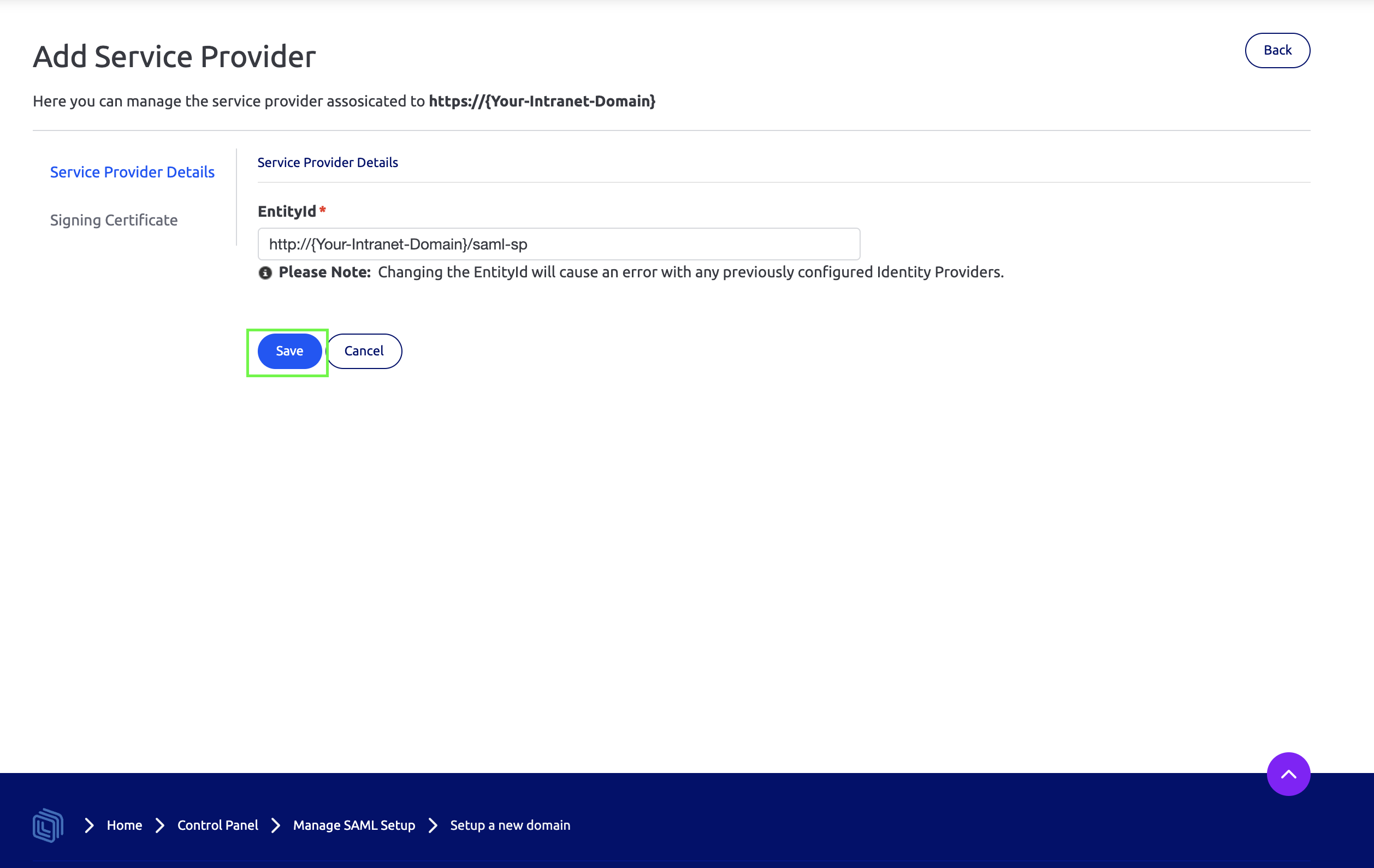
On the next page click Save
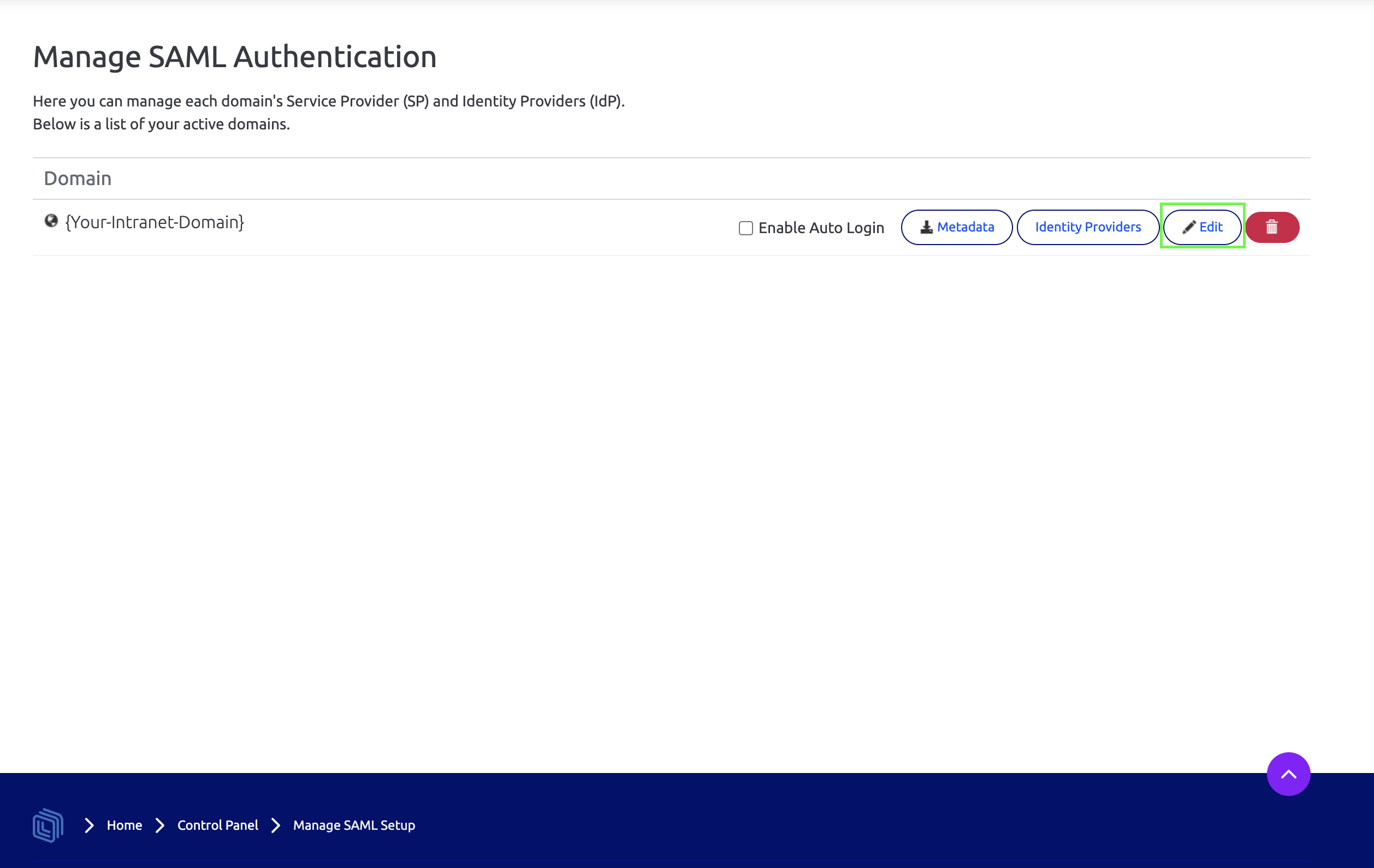
Click the Edit button for the domain you are working against.
On the next screen copy the text of the EntityId.
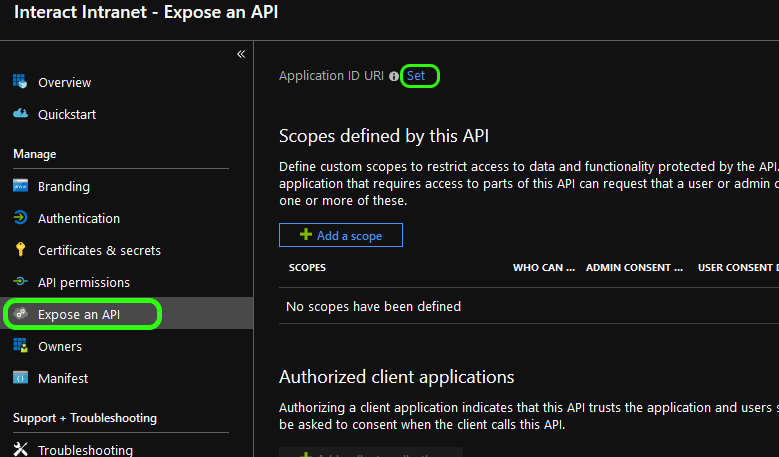
Switch back to your Azure Portal. From the side sub-menu click Expose an API and then, from the main pane, click Set to set the Application ID URI
Paste the EntityId, copied from your Interact settings, into the Application ID URI.
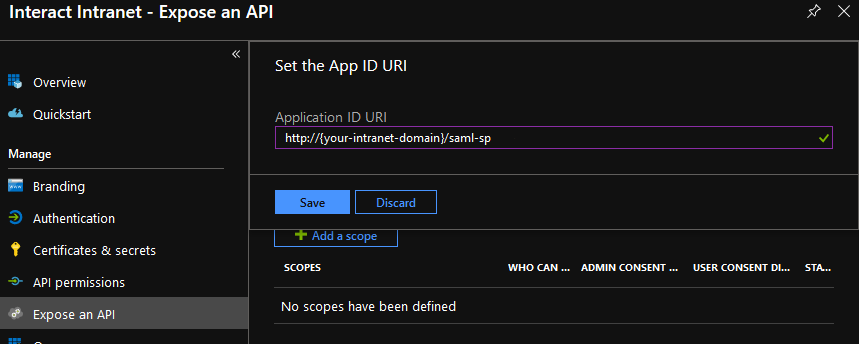
Click Save
Note: If you are using an interactgo.com URL and get an error stating that the domain is not supported, this means that your Azure setup doesn't support this domain. In this case, you need to setup a call like api://{someuniquename} inside the "Set the App ID URI" field. Then you have to copy this value to Interact replacing the existing EntityId with api://{someuniquename}.
5. Meta Data URL
Next you will need your Azure domain name to form the metadata URL. This can be found by clicking Azure Active Directory from the main side menu, then Custom domain names from the sub-menu. Your domain name will be in the pane to the right.
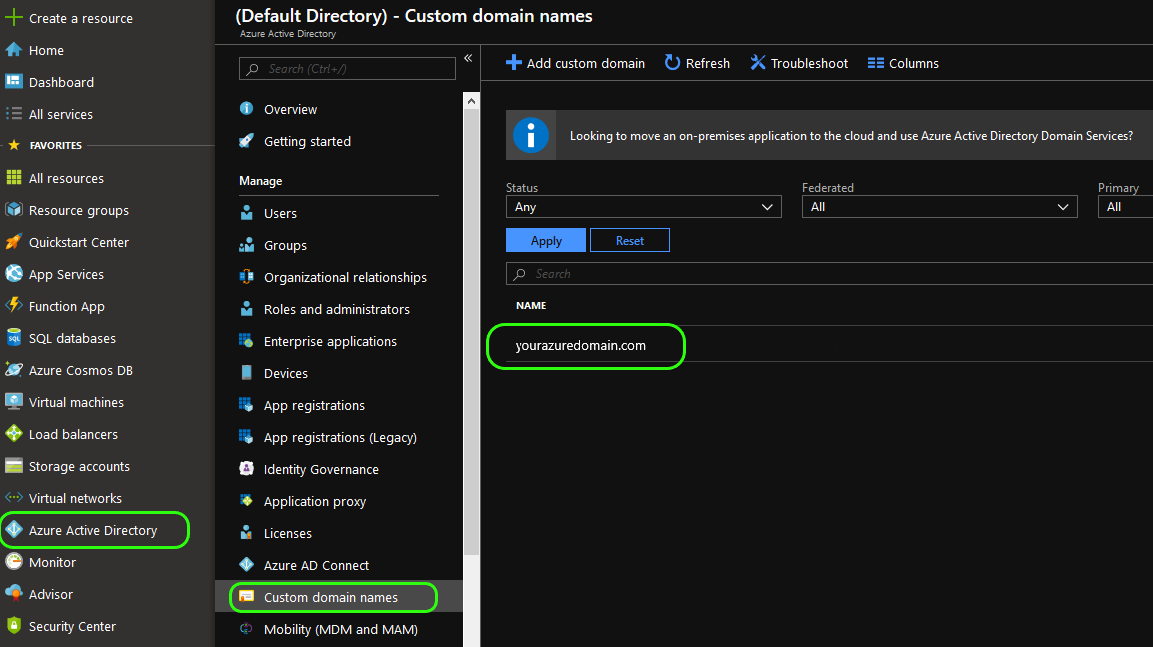
The Azure's metadata URL is formatted as follows:
Replace {your_domain_name} with the name of your domain obtained in the previous step.
6. Create an Idp in Interact
Switch back to your Interact Intranet and again navigate to Control Panel > Manage Security > SAML Authentication.
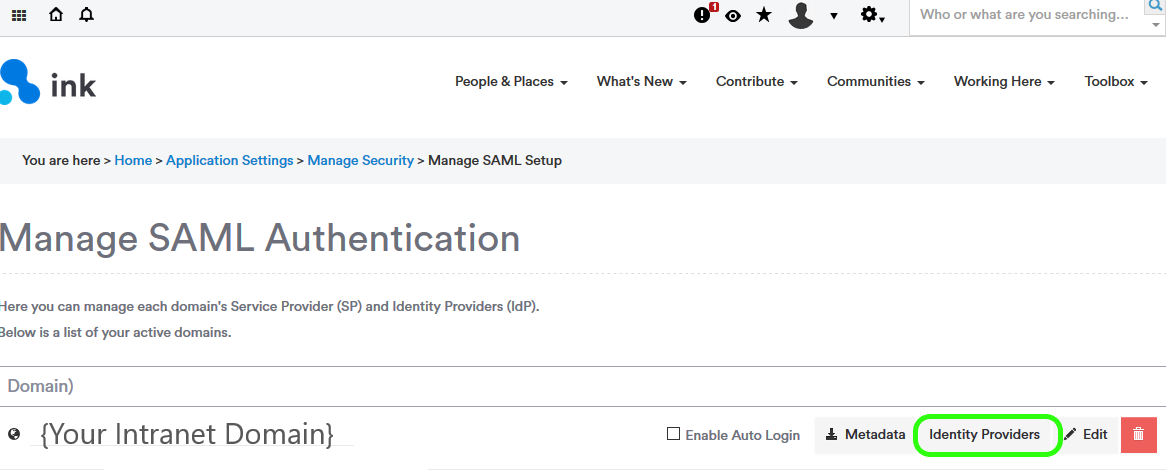
Click the Indentity Providers button
On the next screen, enter the metadata URL you created in step 5 into the Metadata URL textbox, then cick Import as highlighted in the image below.
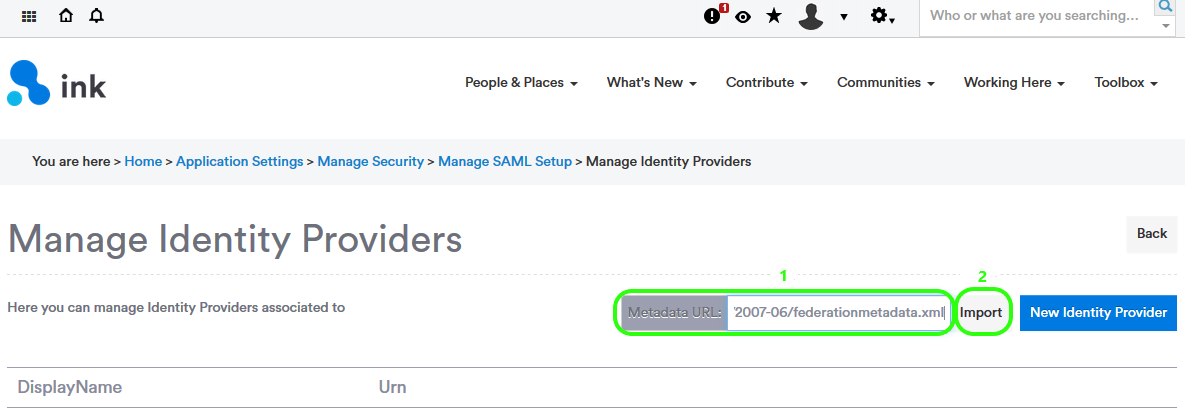
A new Indentity Provider should appear in the list below.
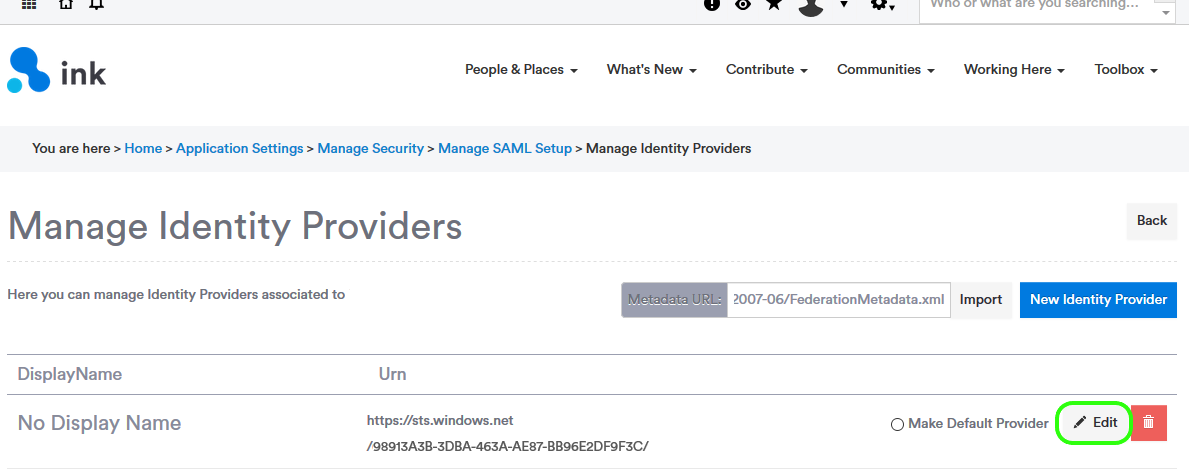
Click Edit for the newly created IdP
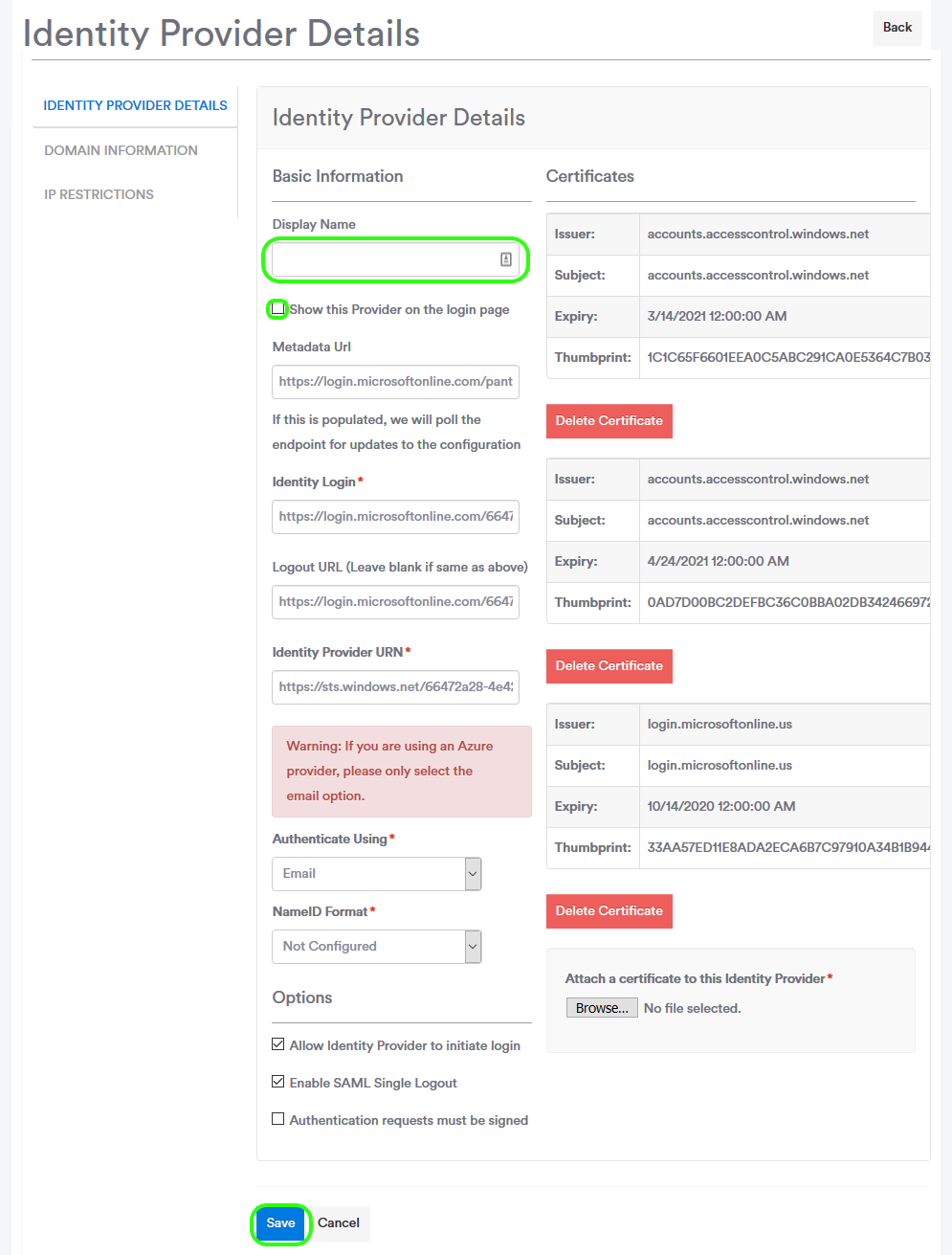
Give the Identity Provider a name and select whether or not you would like it to appear as a button on the Log-In screen for your Intranet. The name your enter here will be the name displayed on button.
Click Save
Thats it! You should now be able to sign into your intranet using your Azure AD credentails.
If you want to enable Seamless SSO (Auto log-in) for this provider. Follow the next step:
6. Auto Sign-in
From the Manage Identity Providers page. Select the option Make Default Provider, then click the Back button located above the blue New Identity Provider button.
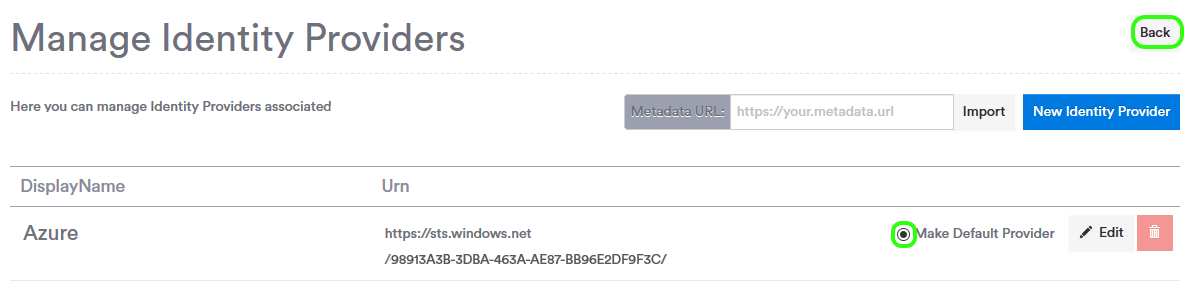
Select the option Enable Auto Login
Troubleshooting
If you get this error below, it is normally because you did not configure "Expose an API" properly. Look at the steps above and ensure that you have http (not https) and the full URL where {your URL is).
AADSTS50011: The reply URL specified in the request does not match the reply URLs configured for the application: 'http://{your URL}/saml-sp'
If you receive this error below, normally you did not properly configure the NameID Format in the "Identity Provider Details" screen within Interact. You need to set the NameID to "Email Address".
Unable to find a user with 'fb7e5ae2-e643-4f38-b872-7cc8237a1c40' as their 'email1' value
If you are generally getting errors and don't know what is happening, you can go to the Manifest within Azure's App Registration. Usually when you look here, the error becomes clear because you are missing some key information in one of the fields.
If you are getting errors with SAML, sometimes this can be caused by having multiples rows within Interact in the "Manage Identity Providers" section. Remove the extra rows so that you are just dealing with one Identity Provider.
Interact caches SAML settings to improve performance, if you make changes you may need to wait ten minutes to allow the cache to be refreshed.
Known Limitations of Azure SAML support
More information on bugs and known issues in Azure SAML setup can be found here:
https://docs.microsoft.com/en-us/troubleshoot/azure/active-directory/troubleshoot-adding-apps
Updated 9 months ago
