Configuring SAML Single Sign On
SAML is one of the methods that can be used to authenticate users logging into your Interact Intranet. You will need to have contacted an Identity Provider or Identity Assertion Provider, who will have provided you with some of the information you will need to fill in as well as sending you a digital certificate.
Using SAML allows your users to log into once to one of your trusted systems and be automatically authenticated in all of the others, reducing the number of times they have to enter their username and password.
Please note, that your users will already need to be set up in the People Directory.
SAML single sign-on is tied to your domain name. If you are currently in your Intranet implementation, please be aware that there is a possibility your core project team will be selecting a custom URL for your site.
If a custom URL is selected, then you will likely need to configure this against both your interactgo domain and the custom URL OR wait until the custom URL is selected.
Please speak with your project team to confirm the approach.
Step 1. Configure SAML SSO in Interact
Navigate to Control Panel. Under Manage Security select SAML Authentication.
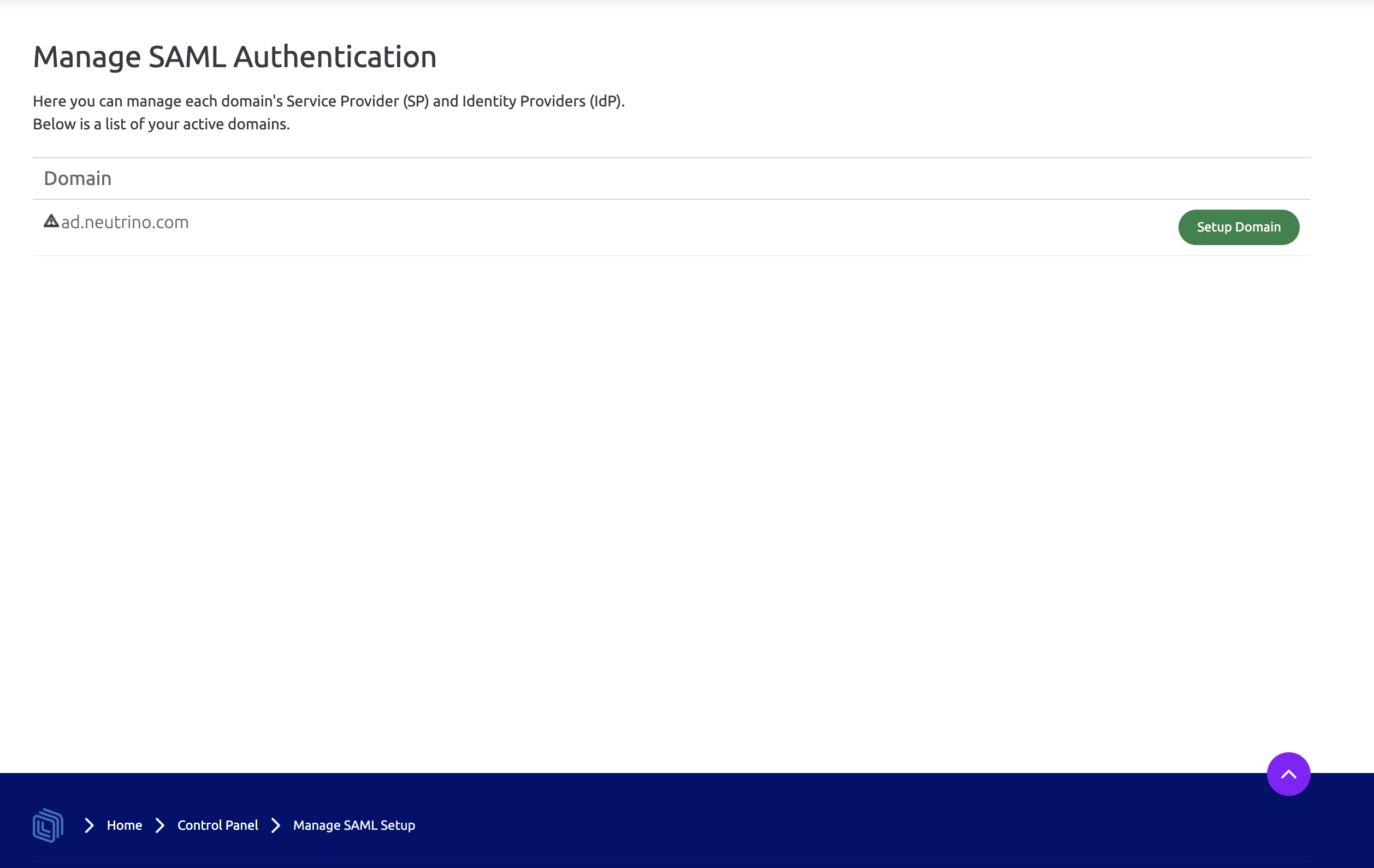
This page lists the domains available to your intranet. Each domain can act as a service provider with its own configuration for authentication. To begin setup of the service provider, simply click Setup Domain next to the relevant URL.
You should see the screen below.
Save this EntityID!Many Identity Providers will need Interact's EntityID, so make sure to keep track of this value while you're configuring SSO. Also, be aware that some providers refer to this as a URN or URI.
The system should populate these fields automatically, so from here, simply clicking "Save" will generate the signing certificate and create the Service Provider details for the specified domain. Once the save process is completed you should be automatically returned to the Manage SAML Authentication page.
Now that the service provider has been created, you can view the Metadata for the service provider, enable auto-login, edit the service provider or configure the Identity Providers.
Step 2. Configure your Identity Provider
Clicking the 'Identity Providers' button will display the screen as shown below. On this page, you can either automatically import an Identity Provider's metadata if available or manually enter the provider's details.
Automatic Import
If the Identity Provider you have chosen facilitates the use of Metadata then you can simply type the metadata URL from the identity provider into the Metadata URL text box and click Import. When using this process, Interact will read the metadata from the specified URL and create the relevant entries for the Identity Provider.
Exchanging Metadata between the Service Provider (Interact) and the Identity Provider is by far the simplest way to set up SAML authentication. Using this process the relevant data is loaded in both systems automatically, including the exchange of certificates and digital signatures.
NoteIf your team authenticates users via a common Identity Provider like Okta, OneLogin, ADFS, Azure AD, or Google G Suite, then please refer to those pages for instructions specific to your provider.
Manual Creation
If Metadata is not available from the Identity Provider, then you must configure this manually. To do this simply click on new Identity Provider. You should be presented with the screen below.
Enter the relevant information for each field. The information required for a successful SAML authentication is presented on the screen in bold and described below. The actual values should be provided by the identity provider.
| Field | Description |
|---|---|
| Identity Login | This should be the login URL for the identity provider |
| Identity Provider URN | This should be the URN supplied by the Identity Provider. This is sometimes referred to as the entity ID |
| Authenticate Using | This tells Interact which field should be used to identify the user once authentication is approved. This needs to match the field that is being sent by the Identity Provider. |
| Attach a certificate to this Identity Provider | Use this field to upload a certificate from the identity provider, used to encrypt portions of the SAML assertion. If using metadata this will be automatically populated and regularly updated automatically by Interact. |
Additional fields that can be used are described below. These provide additional optional functionality.
| Field | Description |
|---|---|
| Display Name | This should be a name for the Identity Provider that makes sense to your users. |
| Show this Provider on the login page | If this checkbox is ticked, a button will be displayed on the login page allowing users to initiate the SAML flow manually. A screenshot of this is included below |
| Metadata Url | If metadata is used to transfer relevant SAML fields, this will be displayed her. |
| Logout URL (Leave blank if same as above) | Interact now supports SAML Single Logoff allowing federated log off as well as federated login. This URL should identify the URL on the identity provider that will trigger the Single LogOff request. |
| Allow Identity Provider to initiate login | If this option is checked, Interact will allow authentication that is initiated by the Identity Provider rather than the Service Provider |
| Enable SAML Single Logout | If this option is checked then users will be able to log off Interact and perform a SAML Single Log Off to also log the off the Identity Provider and any other systems controlled by the identity Provider |
Updated 9 months ago
