With ADFS
In order to configure Interact with ADFS for SAML single sign-on, follow the simple instructions outlined below.
Step 1: Configure SAML SSO in Interact
The first thing that needs to be completed is the creation of the SAML Authentication source within Interact. Follow the steps on the Configuring SAML Single Sign On page to enable a SAML service provider for your domain.
Step 2. Configure ADFS
In ADFS, add a Relying Party Trust.
Navigate to Trust Relationships > Relying Party Trust, and choose Add Relying Party Trust.
Proceed by clicking Start
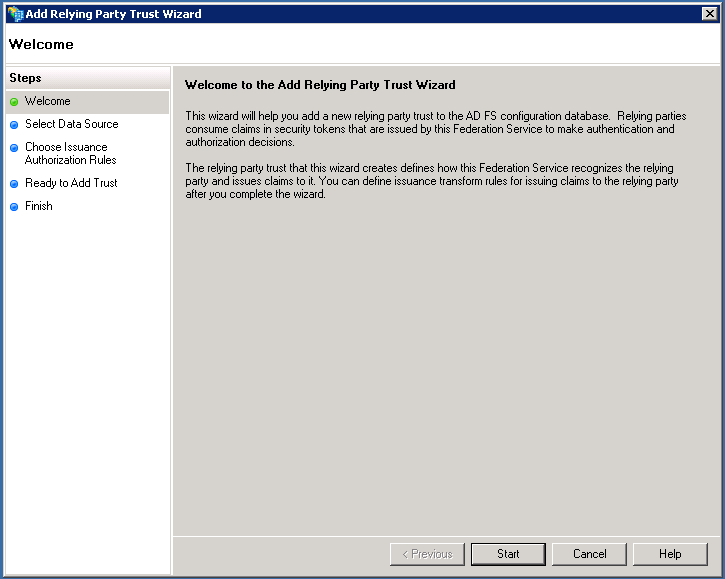
Automatic import of Interact's SP Metadata
Interact supports the use of federation Metadata for automatically loading the Service Provider settings into the relevant Identity Provider (in this case ADFS).
In order to use federation Metadata, simply enter the URL for your metadata definition as described in the Metadata page, into the first textbox on the screen below, and work through the remainder of the Wizard.
That's it. Move onto Step 3.
Manual Configuration of relying party
Alternatively, you can enter the data manually into ADFS by selecting the “Enter the data about relying party manually” and continue
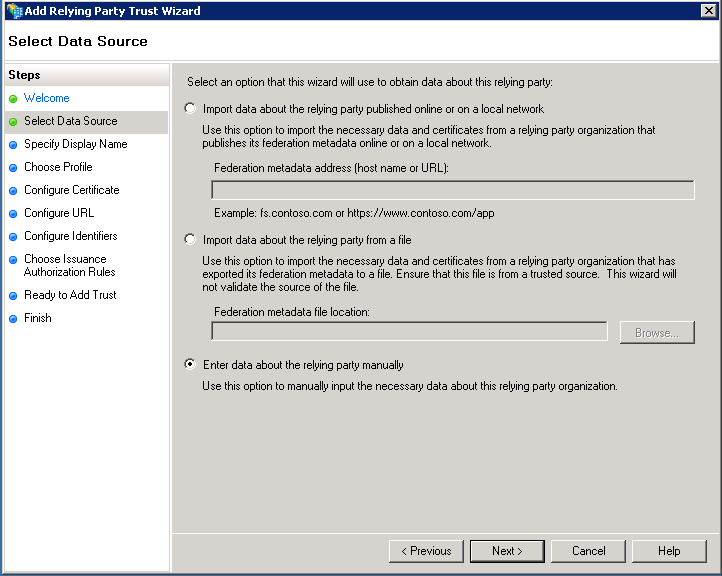
Specify a display name of your choice.
Select ADFS 2.0 profile and continue
The optional token encryption certificate is not required by Interact and this step should be skipped.
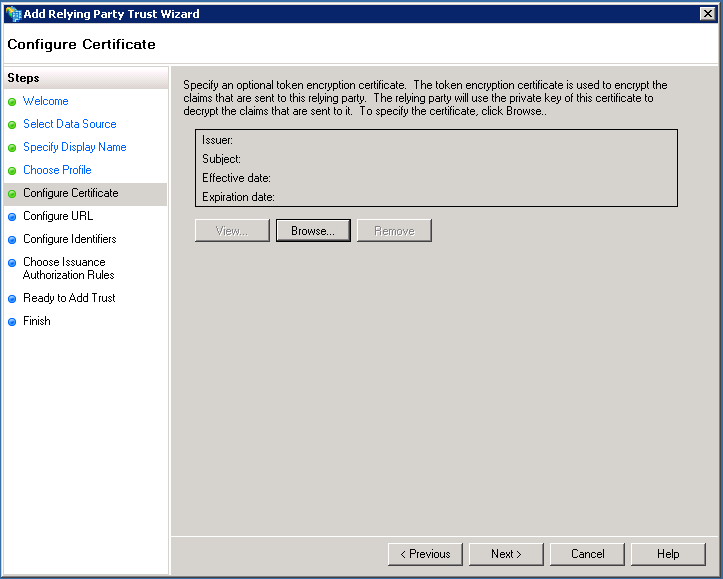
Check Enable support for the SAML 2.0 WebSSO protocol and add the relevant url:
https://<fully qualified domain>/Interact/Login/default.aspx
Please note this url is case sensitive
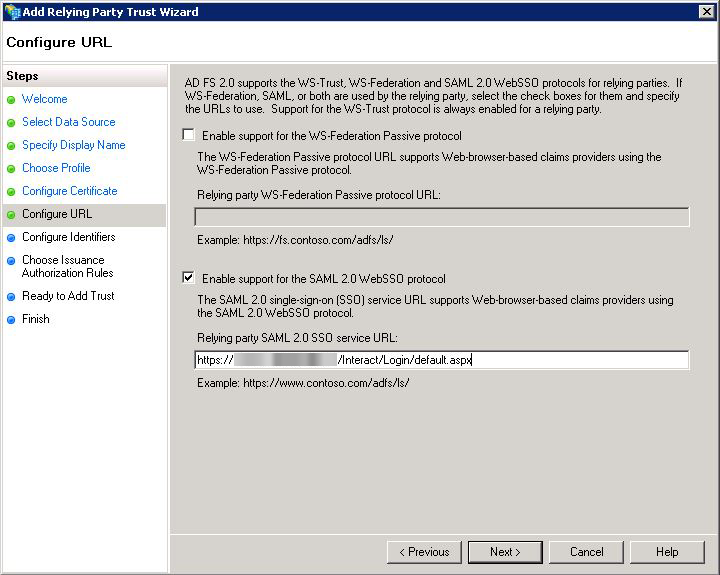
Add the relevant replying trust identifier. This can be obtained from the Manage SAML Authentication area within Interact (see Item 2 in the Interact Configuration section of this document).
Ensure that Permit all users to access this relay party is checked and continue.
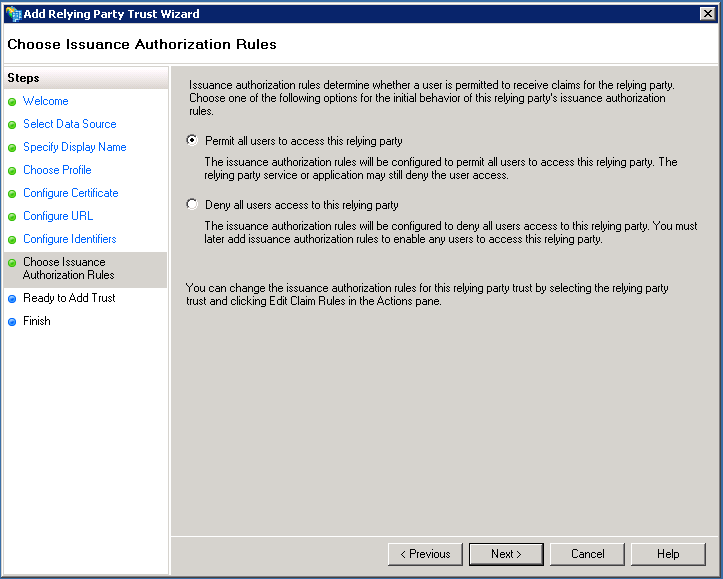
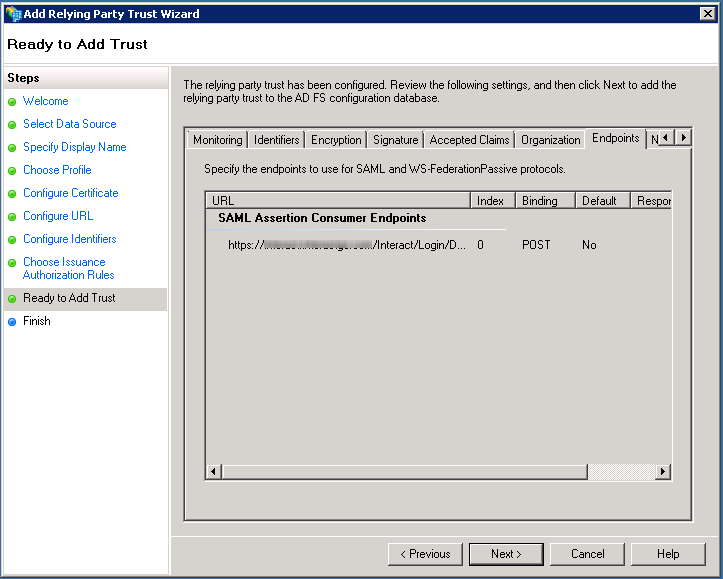
Check that Binding is set to POST within the Endpoint tab before continuing by selecting Next
Open the Edit Claim Rules when ending the wizard
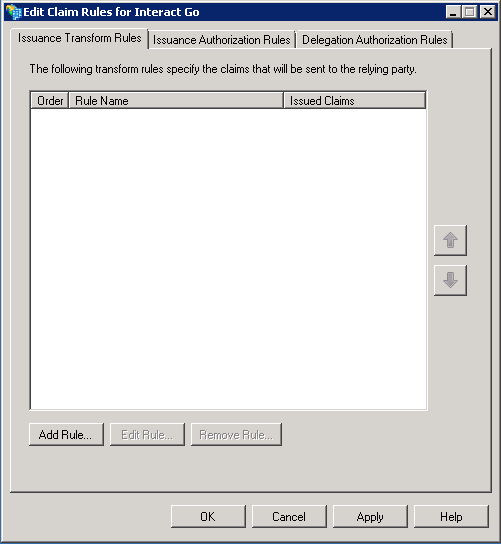
Claim Rules
Within the Edit Claim Rules dialog, select Add Rule
Select “Send LDAP attributes as Claims” as the Claim rule template
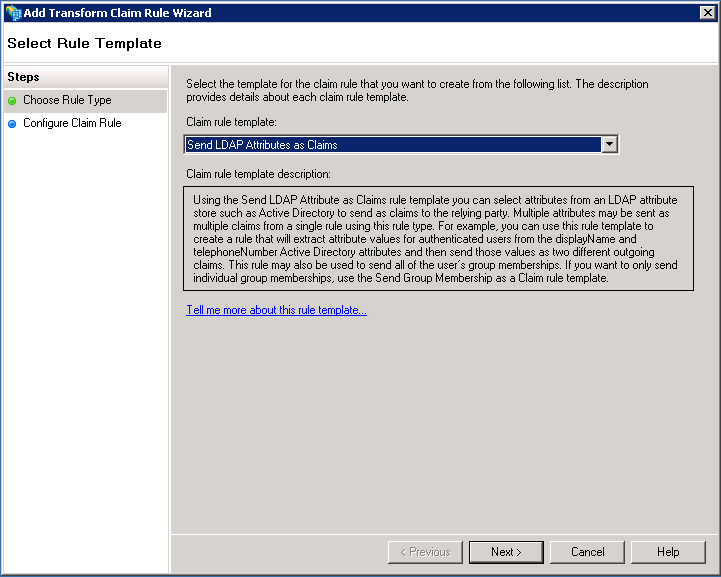
Specify the following properties for the new Claim Rule
| Property | Value |
|---|---|
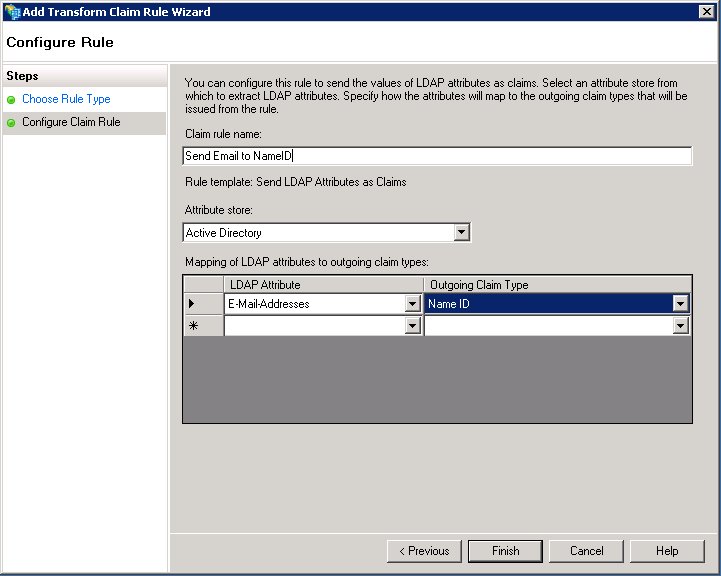
| Claim rule name | Send Email to NameID |
| Attribute store | Active Directory |
| LDAP Attribute | E-Mail-Addresses |
| Outgoing Claim Type | Name ID |
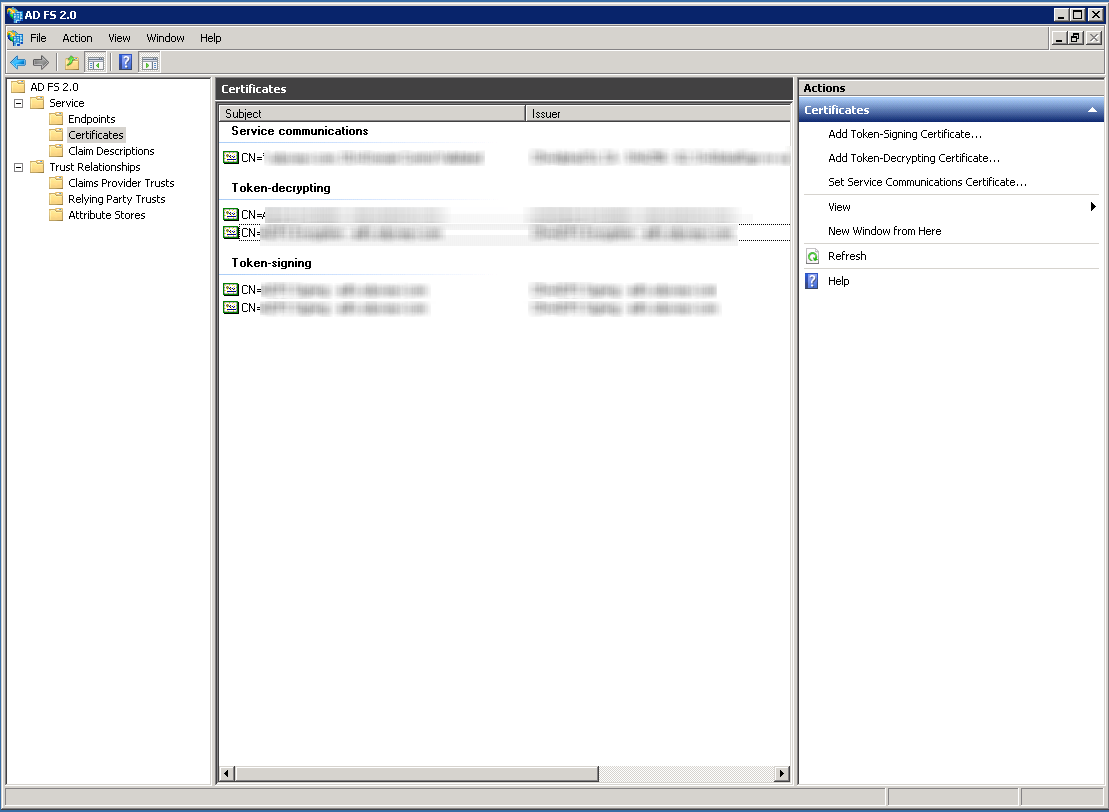
Certificates
You will need to export your Token-signing certificate from ADFS, In ADFS, go to Service > Certificates, open the details for the token signing certificate, go to the Details tab and select Copy to File...
Step 3. Import ADFS Metadata in Interact
Automatic import of IdP Metadata
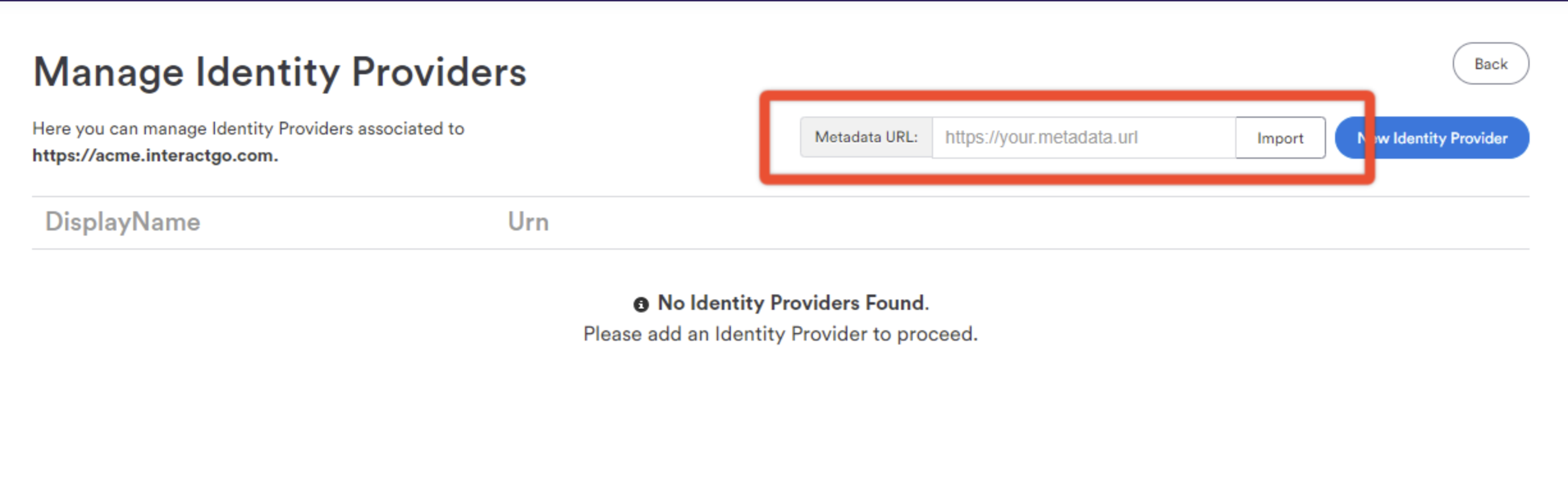
- As a power user, navigate to Control Panel > Manage Security > SAML Authentication.
- Ensure that SAML is enabled for your domain. See this page for more details.
- Click on "Identity Providers"
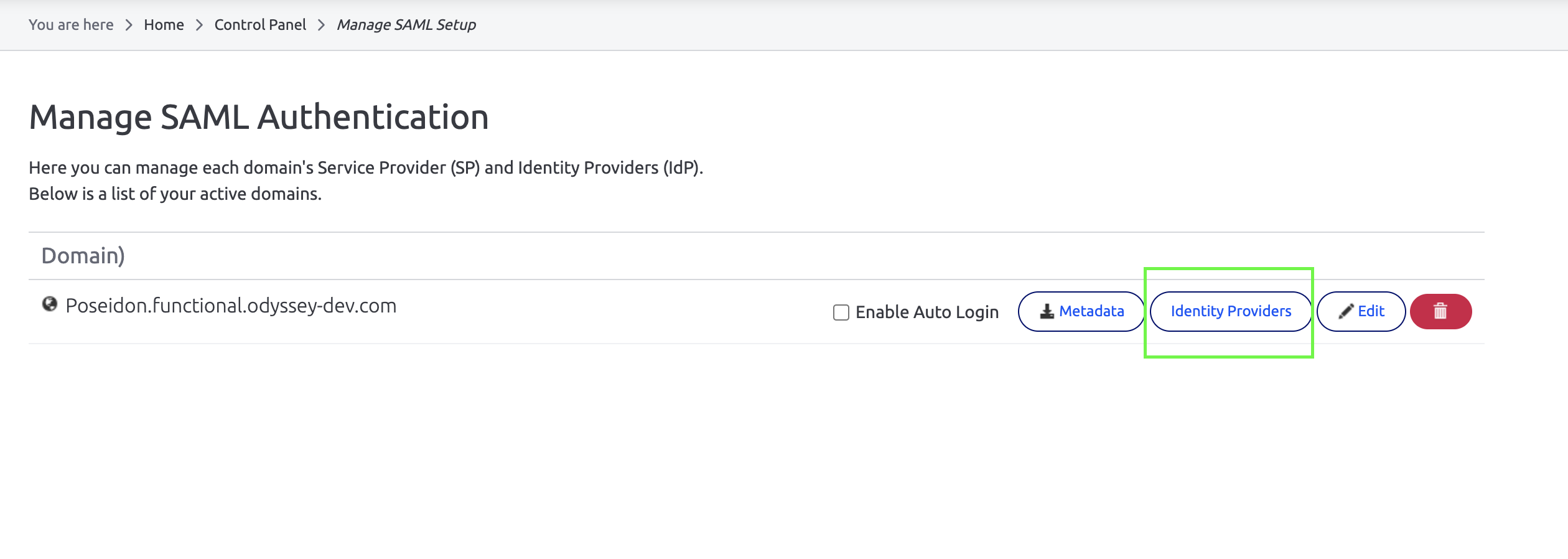
- Paste your AD FS Federation metadata endpoint URL and click import.
Manual Configuration of IdP in Interact
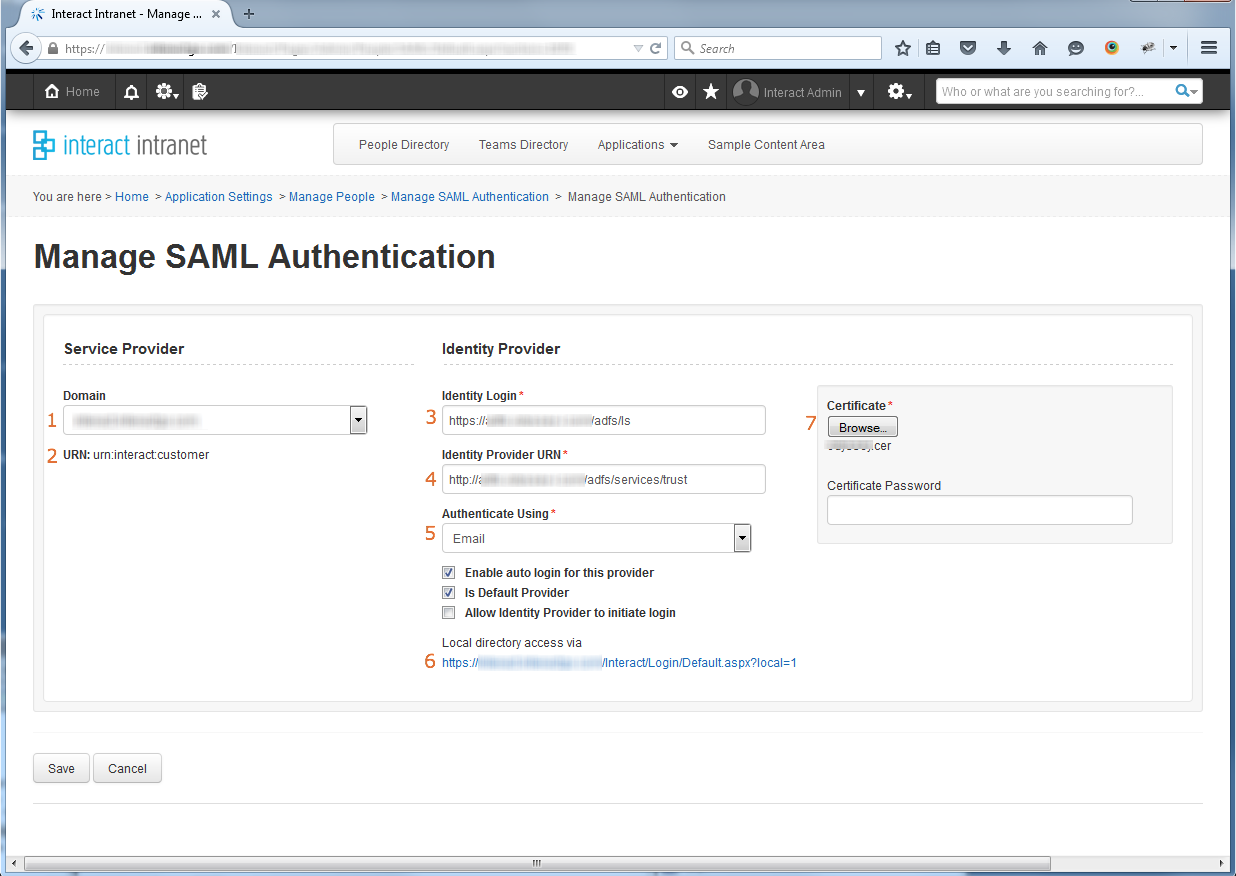
- Specify the primary domain for Interact, in most instances, you will only have one domain to select from.
- This is the auto-generated Relay Trust identifier that should be specified within ADFS setup.
- Specify the URL of the ADFS Federation Service End Point in the format: https://fully_quailfied_domain_name/adfs/ls
- Specify the URL of the ADFS Federation Service Identifier in the format: http://fully_quailfied_domain_name/adfs/services/trust
- This should be set to Email.
- This URL can be used to access Interact using local directory credentials and bypass ADFS SSO
- Upload the token-signing certificate from ADFS
Troubleshooting
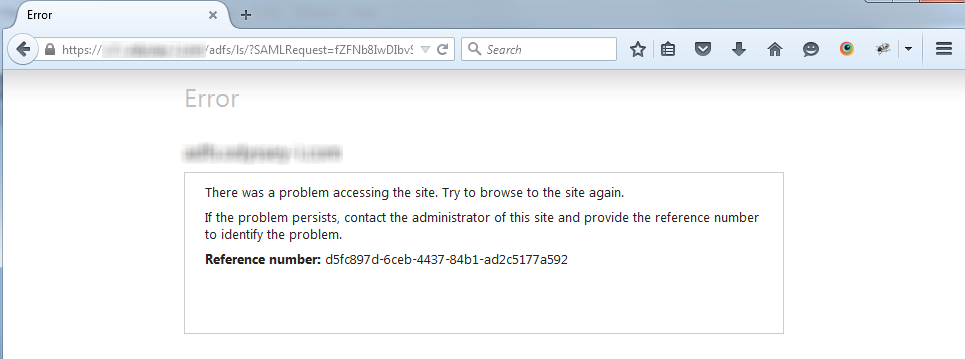
ADFS is displaying an error
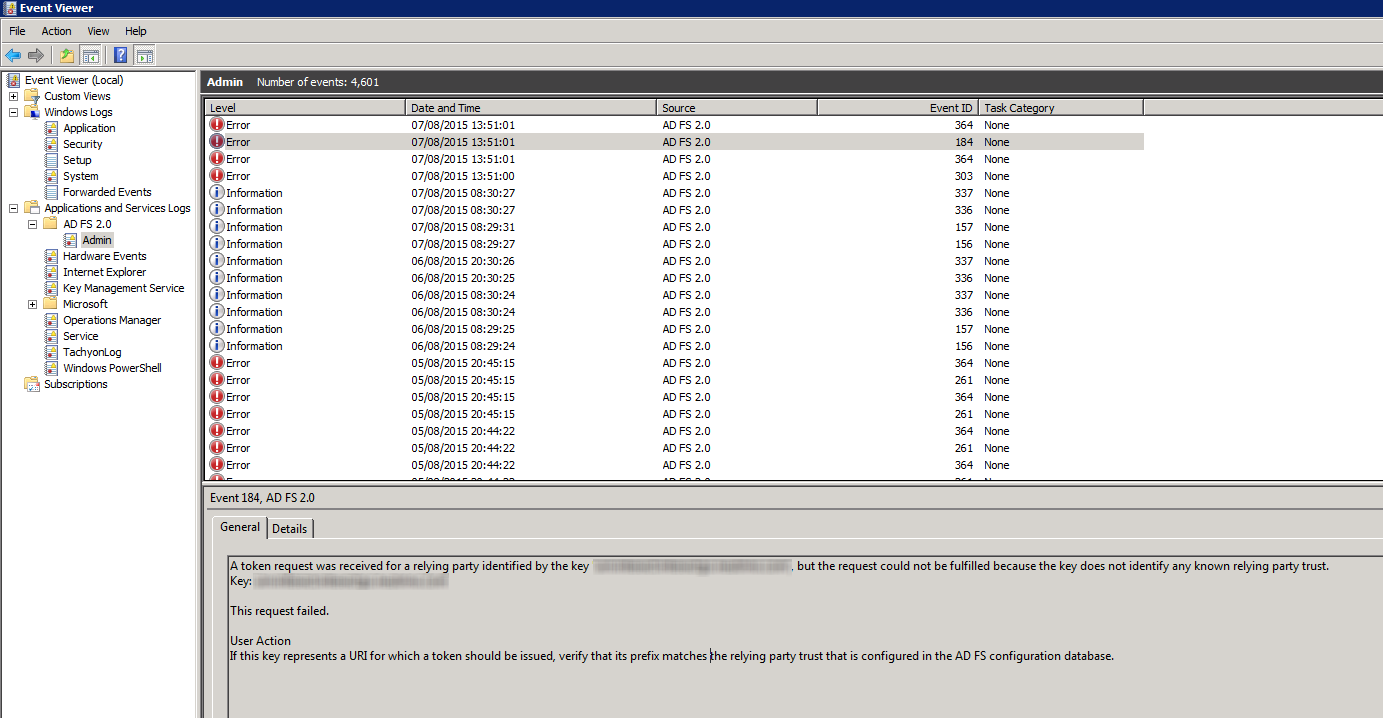
In the event of configuration error within ADFS, the user will be presented with an error message similar to the one shown below. The Event Log on the ADFS server can be queried using the reference number shown.
ADFS is authenticating successfully however Interact is displaying the Login Page.
Interact suppresses any errors reported when interacting with ADFS and therefore in the event of an error displays the Interact login screen. Errors are recorded and accessible to the Interact Support Desk, so please contact the Support Desk for more information.
If there are no relevant errors within the log it is possible that there may be an issue with the individual user. Ensure they have an active account, the email address stored against their profile matches the one within Active Directory. Finally, ensure that their profile within Interact is setup for SAML authentication.
Updated 9 months ago
