Configuring MS Teams for Interact
This guide will enable you to add your Intranet into MS Teams. Your Intranet will be accessible in MS Teams Desktop, MS Teams Web and the MS Teams mobile application.
Overview
You will need to do the following activities:
- Create a new Enterprise application within Azure Portal
- Configure Interact for Teams authentication
Azure Settings
Create a new Enterprise application within Azure with the following settings.
Navigate to overview/app registrations & click create new registration.
Enter application name, this can be anything suitable for the application.
Select single-tenant account types, to ensure only accounts within your organisation can use the teams application.
The page must be set up as a single page application
In the section titled "Redirect URI (Optional)"
- Select single-page application (SPA)
- Enter value
https://{Your_Intranet_URL}/MicrosoftTeams/Display
Click Register
Authentication
The MS Teams integration requires the Teams login to authenticate against the user's email address associated with their intranet profile. If the Teams login and the intranet profile email addresses differ, a blank screen will be displayed when the intranet is opened in Teams.
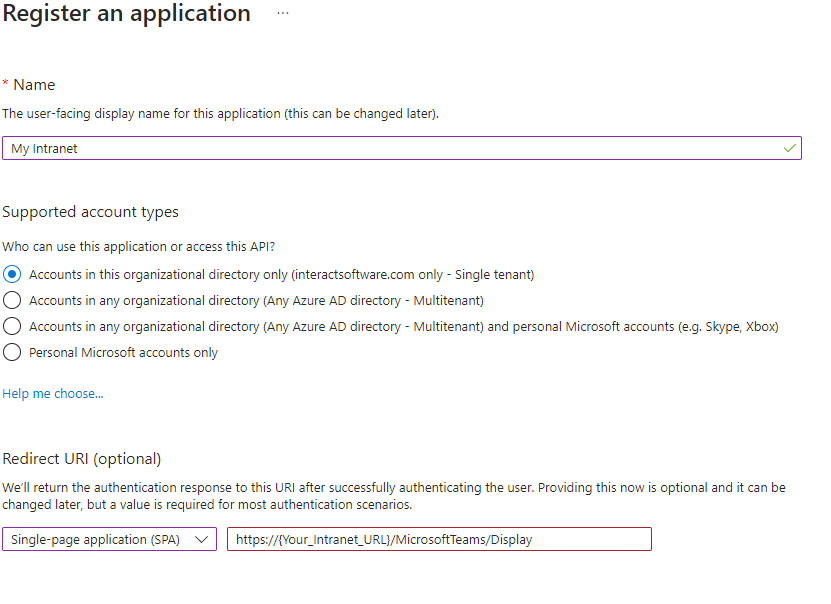
- Navigate to the Authentication tab
- Enable Access Tokens & ID tokens.
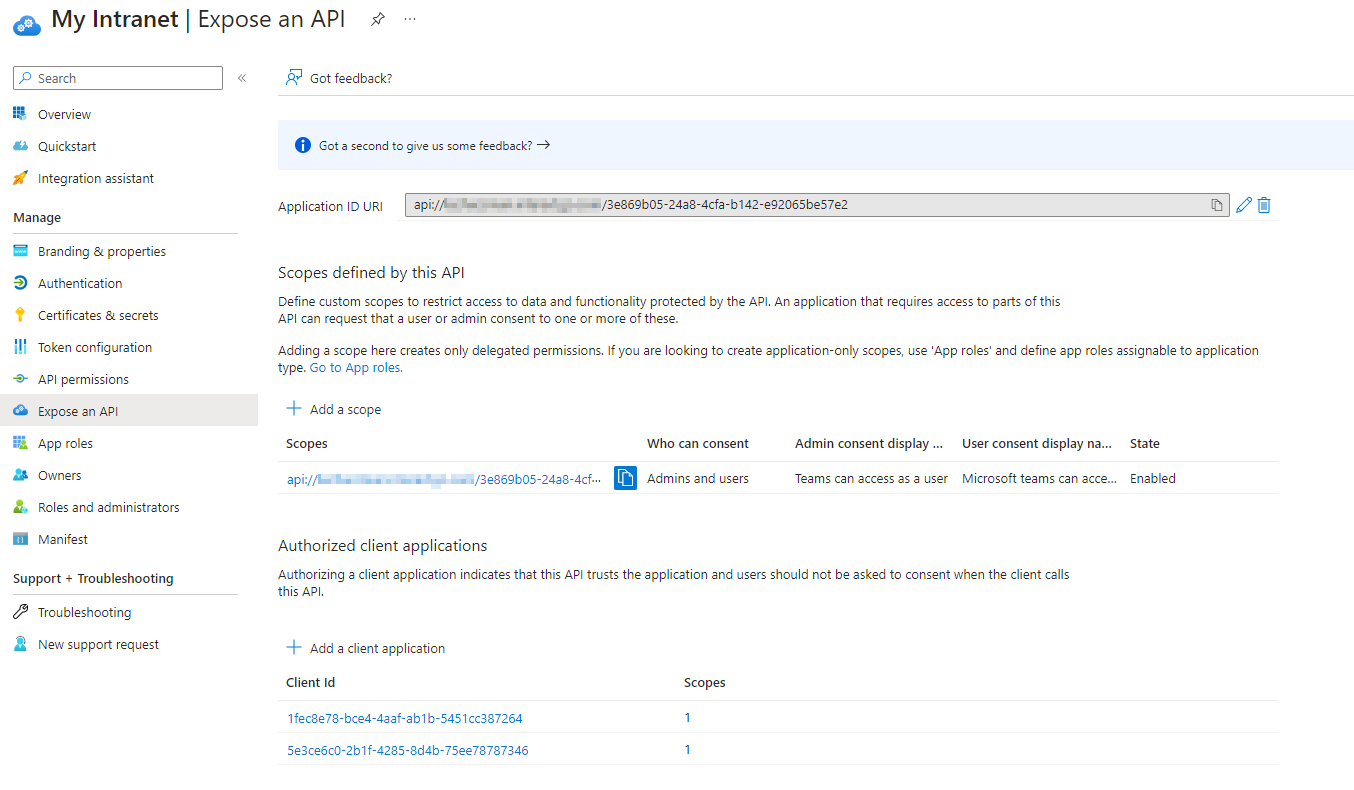
Expose an API
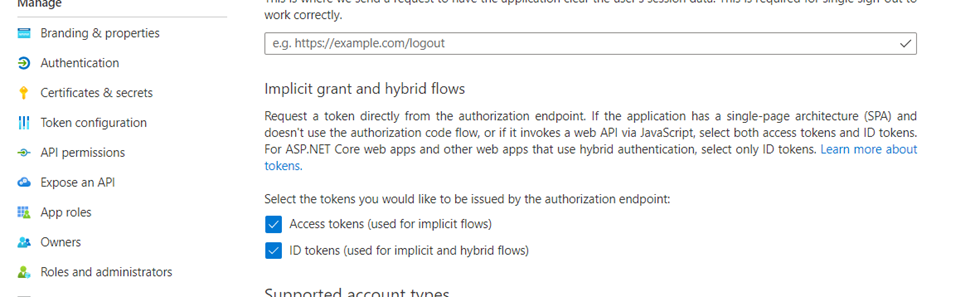
Navigate to the Expose an API tab.
Application ID URI
Click Set to configure the Application ID URI
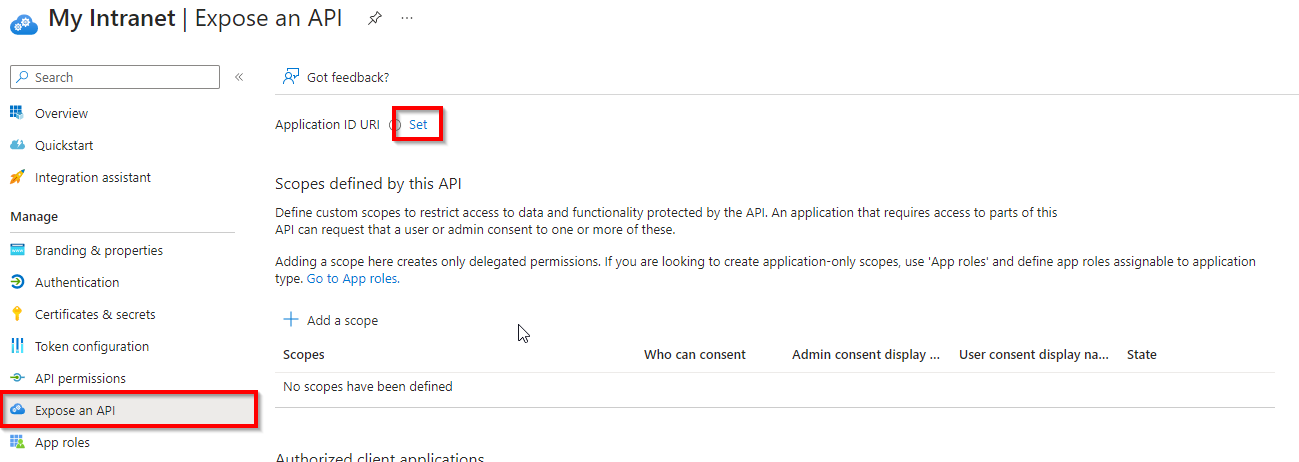
api://{Your_Intranet_URL}/3e869b05-24a8-4cfa-b142-e92065be57e2 - It will automatically suggest a new GUID which can be used.
Scope
Click Add a scope
access_as_user
This scope is utilised by the Teams Authentication Library and must be in this exact format as shown below.
Authorized client applications
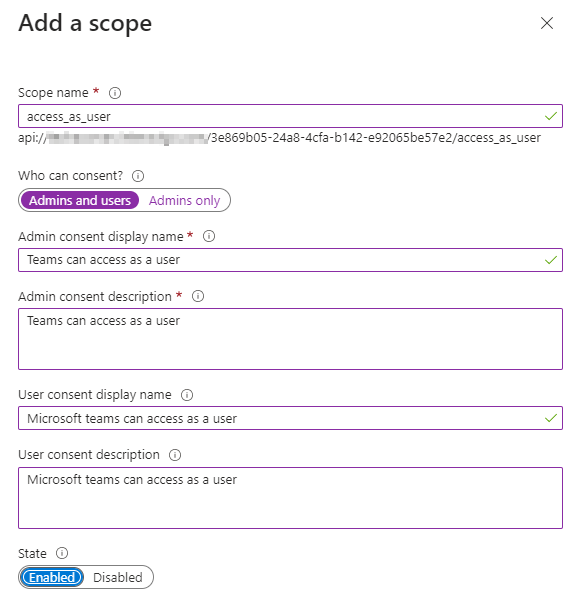
Click Add a client application
Add both of the GUID's below (one at a time). You must use these GUID's as they are listed below, they are standard MS Teams GUID's for the Interact application.
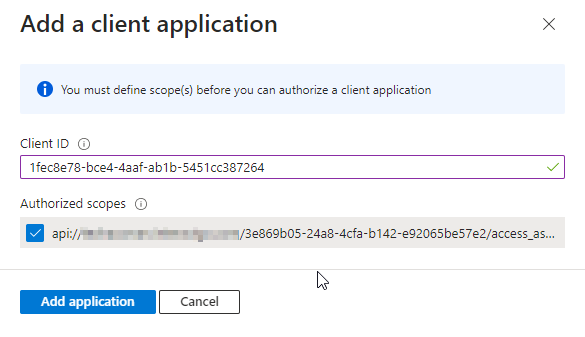
1fec8e78-bce4-4aaf-ab1b-5451cc387264← Team Mobile/Desktop app5e3ce6c0-2b1f-4285-8d4b-75ee78787346← Teams Web app
The page should now look like this...
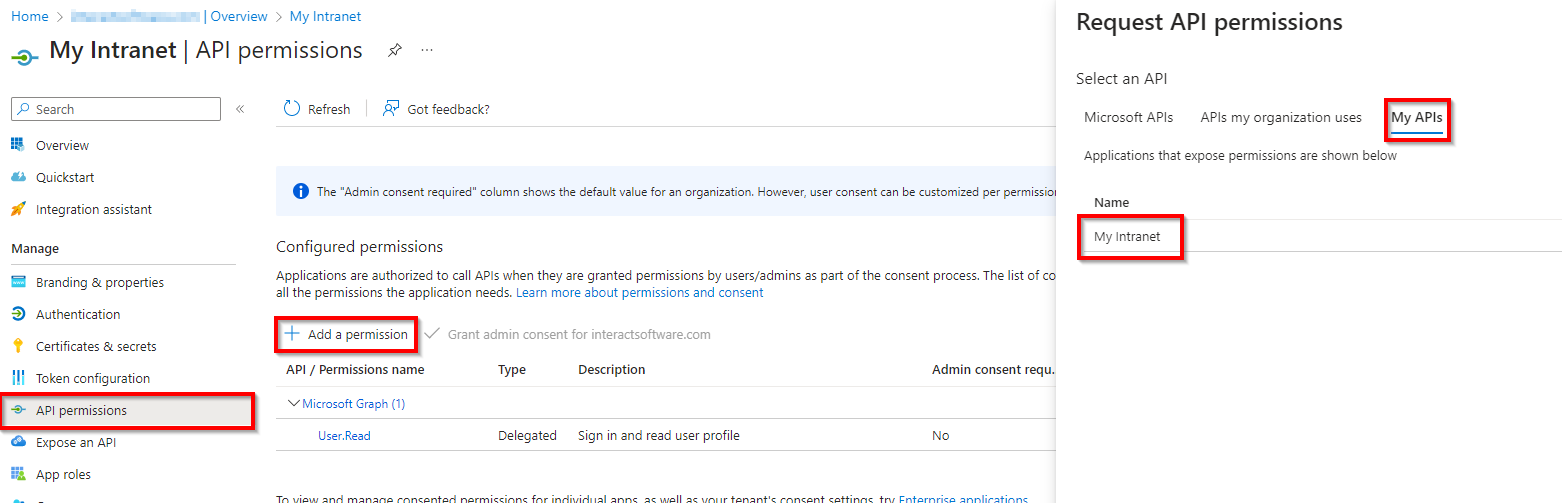
Api Permissions
Add the following permission: access_as_user which will have become available since adding it as a scope in the previous section. This scope is utilised by the Microsoft Teams Authentication Library, therefore required to access the user from the Teams client.
Click Add a permission > My APIs tab > Click on the newly created application name
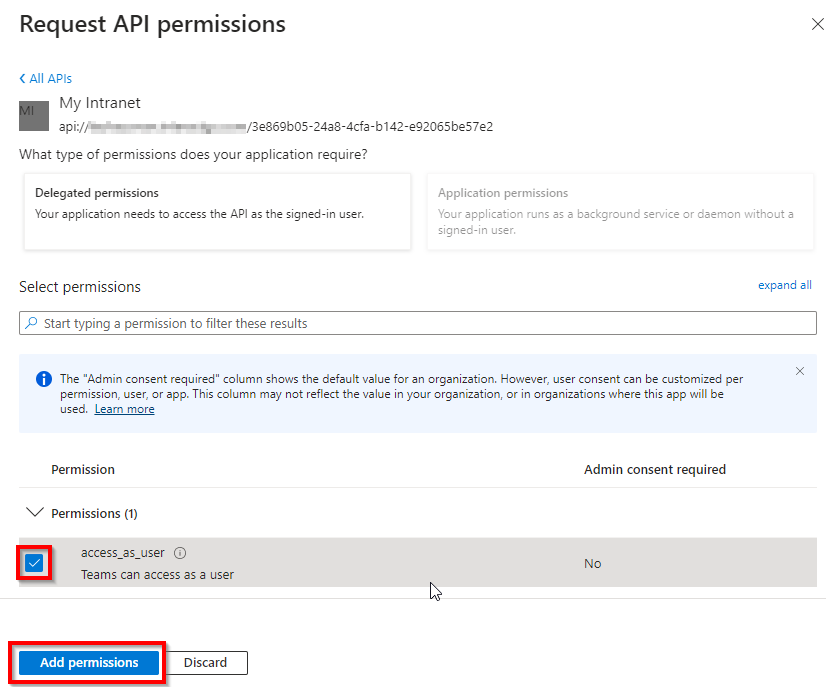
- Tick the access_as_user Checkbox
- Add permissions
Configuring Interact for Teams MSAL Settings
The settings required for Teams authentication are found at
Control Panel > Manage Security > MSAL Authentication
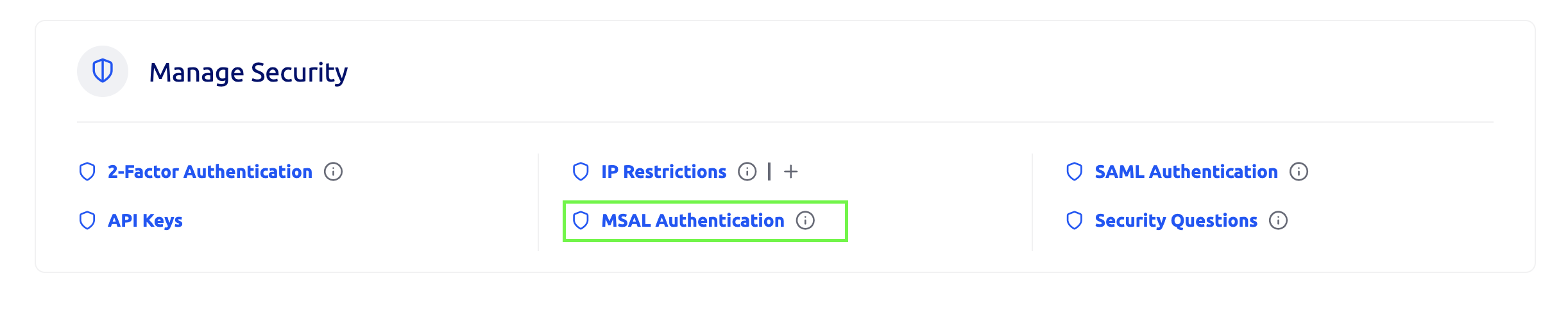
A new Teams configuration can be set here to allow a Teams user to authenticate silently against their intranet and load it up as an integrated Teams App within Teams Desktop/Mobile/Web app as below. The application title will match the name configured for the integration.
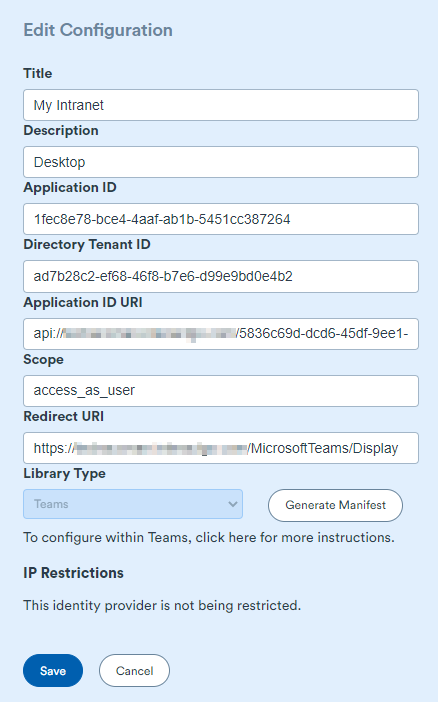
Title: Can be any relevant name for the application. This will be used as the name of the application within Teams.
-
Description: Will also populate the Teams application description.
-
Application ID is the Client ID of the application. We are integrating into Teams which has the following 2 Client IDs:
1fec8e78-bce4-4aaf-ab1b-5451cc387264← Team Mobile/Desktop app5e3ce6c0-2b1f-4285-8d4b-75ee78787346← Teams Web app
-
Directory Tenant ID is the Tenant ID can be found in the Azure App registration
-
Application ID URI: Can be found on the overview page of the azure app registration. It is uses the following format:
api://{Site domain}/5e3ce6c0-2b1f-4285-8d4b-75ee78787346
-
Scope: Must be access_as_user as this is the scope used by Microsoft Teams.
-
Redirect URI: This is the location of the Teams Application view. It can be found at:
https://{site domain}/microsoftTeams/Display
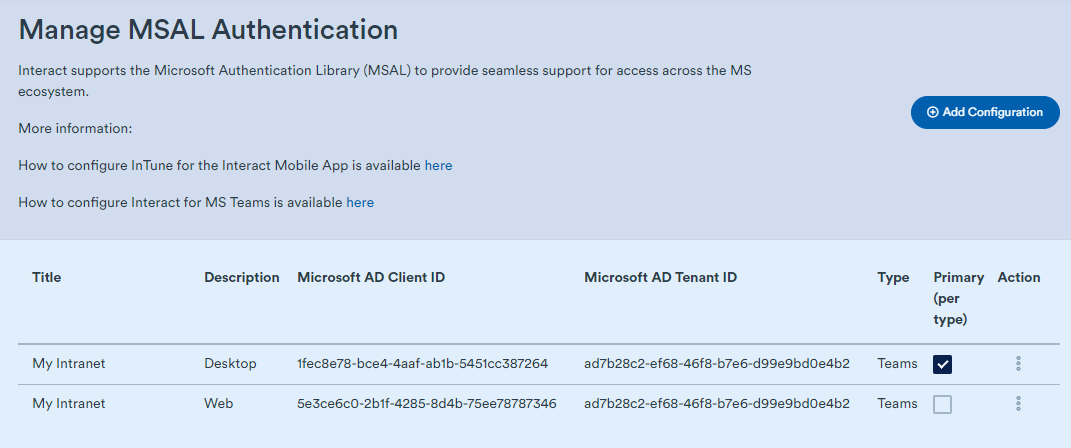
Once complete, save, then reopen the edit page (click the 3 dots). There should now be a "Generate Manifest" button. Click to generate a manifest for Microsoft Teams Integration. Follow the next phase of set up which can be found here: Generate Manifest
Once those steps are complete, please contact our Technical Support team, who will perform one final step before making your intranet available in the Teams App.
File DownloadsIt should be noted that downloading files from Interact is not available through the MS Teams app in either the browser or the Teams Apps.
Updated 9 months ago
